Protect, Advance and Enable Your Organization with
Steeves and Associates

Steeves and Associates has received engineering-led training from Microsoft to deliver valuable Cloud Accelerator and Microsoft Security workshops to educate, empower and enable your team to:
- Confidently adopt cloud & security solutions
- Secure your organization
- Drive implementation efficiencies
- Improve communication
- Transition to the Cloud
Whether you’re looking for expert help to plan, configure or succeed with Endpoint Management, Microsoft Teams, Microsoft 365, Azure Sentinel, Microsoft Security, Data Protection, or more, we’ve got an informative workshop that’s tailored to your environment waiting for you!
Select a Workshop Below to Learn More:
Our Clients Say it Best

“The workshop helped us to get a good overview of the very complex Microsoft 365 security environment. Steeves and Associates stepped in to give us expert insights on how to tune every system and make optimal configurations to meet our cloud security requirements. The Microsoft Security workshop has been useful in reducing the confusion and debate around which configuration changes to make and has allowed us to move ahead much more quickly.”
– Hugh Burley, Director Information Security, Thompson Rivers University.
Explore Our Current Microsoft Security Workshops
Endpoint Management Workshop
Manage & protect your devices, your apps, and your users.
Equip and enable your team with the training they need to manage users’ devices, apps, and identities from anywhere.
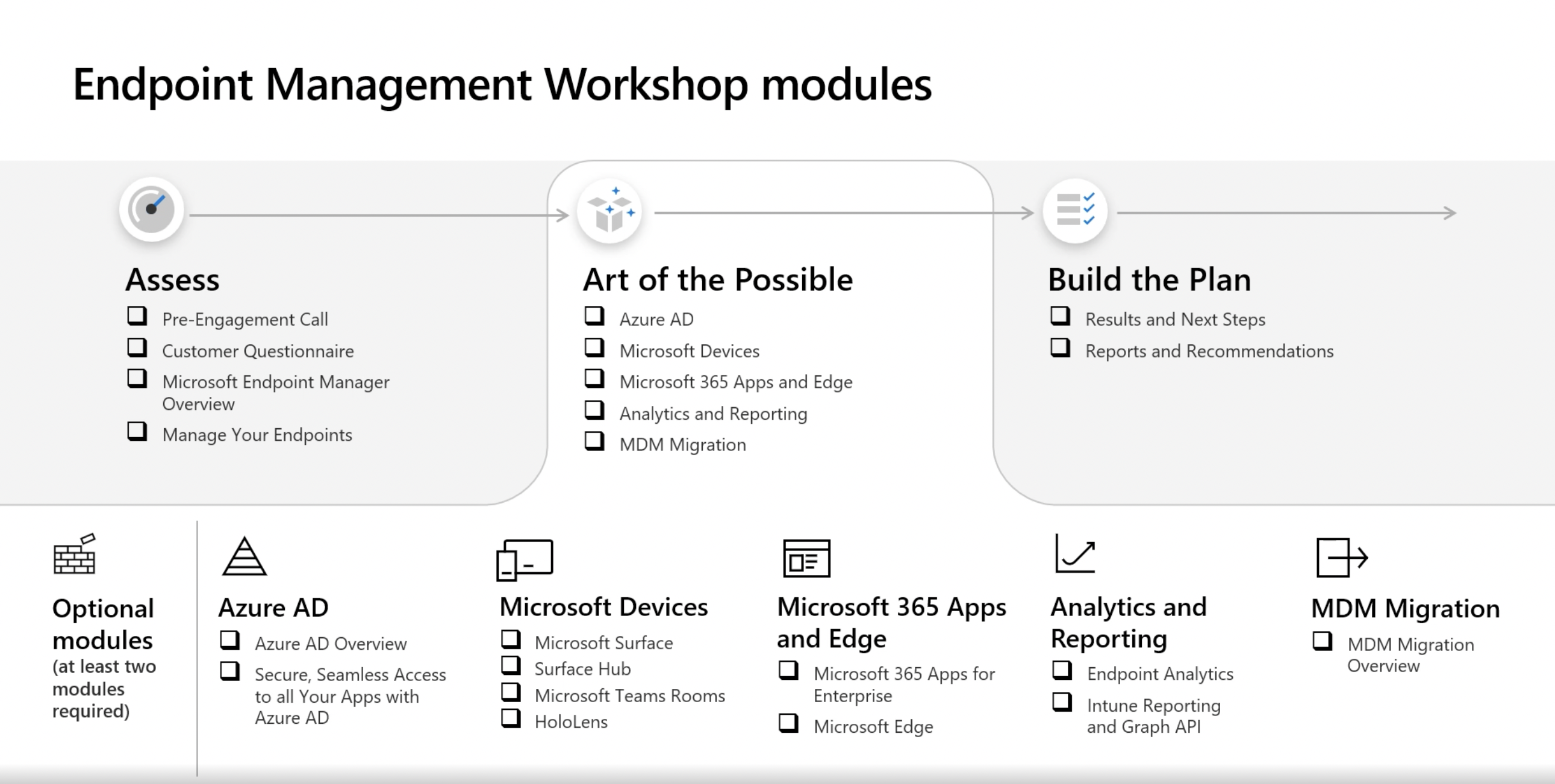
Join us for an interactive Endpoint Management workshop to:
- Learn how to improve current endpoint and device management with best practices.
- Discover existing endpoints using your tenant capabilities, and how to protect your organization.
- Secure identities with MFA and automatic, risk-based conditional access from any device.
- Enable workforce productivity by providing access to apps on whichever device users choose.
Book your Endpoint Management Workshop today >>
Threat Protection Workshop
Learn how to leverage next-generation Microsoft security tools for your specific organizational needs.
Steeves and Associates works with you to develop a threat protection strategy customized for your organization and based on the recommendations of Microsoft cybersecurity experts uses a specialized Threat Check SKU for identifying real-time threats to your organization.
During this workshop you can expect to:
- Gain insights from a security expert on your priorities, initiatives and security strategy.
- Explore threats to your specific environment across email, identity, and data.
- Discover the optimal approach to Microsoft security with an interactive experience.
- Plan for the next steps required to remediate security gaps in your environment.
Book your Threat Protection Workshop today >>
Azure Sentinel Workshop
Gain a bird’s eye view across your enterprise with security information event management (SIEM) and see and stop threats before they cause harm.
Join us for this workshop to learn more about Azure Sentinel along with insights on active threats to your Microsoft 365 cloud and on-premises environments.
In this workshop, we’ll work with you to:
- Analyze your requirements and priorities for SIEM deployment.
- Define scope and deploy Azure Sentinel in your production environment.
- Explore remote monitoring and proactive threat hunting.
- Discover threats and demonstrate how to automate responses.
- Recommendations on next steps on how to proceed with Azure Sentinel.
Book your Azure Sentinel Workshop today >>
Securing Identities Workshop
Gain awareness of suspicious user and sign-in behavior and get ahead of ongoing suspicious requests.
In this workshop, Steeves and Associates will help you identify risks happening now in your environment, gain insights on your application landscape, and improve your identity security posture.
In this workshop, we’ll work with you to:
- Understand your identity goals and objectives.
- Define your existing and desired identity security posture.
- Provide insights into applications used within your environment
- Showcase core IT and user security scenarios through demos.
- Develop a joint action plan based on key results, recommendations and next steps.





