Cyber attacks, Data Breaches & Malware…Oh My: How to Better Protect Your Data in Microsoft 365 & Azure
The risk of a data breach and cyber attack on your organization’s confidential business information grows daily with cybercrime well and truly on the rise. To combat this, organizations must take the necessary steps to enhance enterprise security to proactively reduce their risk exposure. A recent study by McKinsey reported that:
- The average cost of a data breach is $3.5 million to an organization.
- The majority of breaches (63%) are a result of weak or stolen passwords.
- 87% of Senior Managers have admitted to accidentally leaking business data.
According to Microsoft, 80% of security breaches involve privileged credentials. Accounts with privileged credentials have access to sensitive organizational information and are at a much higher risk of causing significant organizational damage if infiltrated. In a recent Deloitte cyber attack, hackers managed to obtain access through a privileged email account.

The State of Enterprise Security Today
Most organizations are using Office 365, Windows 10 and/or Azure but aren’t aware of the built-in security and data protection functionality readily available with these platforms, which can be utilized to better protect organizational data, identity and infrastructure.
Organizations are experiencing tremendous benefits and efficiencies with enterprise technology but many are lagging behind when it comes to enterprise security and data protection. Security breaches are all around us and the damage from data loss, loss of customer trust, identity theft, impersonation and financial loss is growing at an alarming rate.
With technology impacting almost every part of an enterprise organization in one form or another, the onus of implementing and ensuring adequate data security and information protection lies with senior management, the CEO specifically, according to McKinsey.
What is a Cyber Attack and What Does it Entail?
According to IBM, a cyber attack is ‘the deliberate exploitation of computer systems and networks using malicious software (malware) to compromise data or disable operations.’ Cyber crimes such as information theft, fraud and ransomware attacks are all enabled by cyber attacks.
Ransomware attacks are becoming increasingly popular, with the City of Albany becoming the latest victim, causing the police department to return to note taking with a pen and paper. Police were left with no access to important files and information as the data has been encrypted by the attackers, demanding a ransom for its decryption. Interestingly, a lot of ransomware takes place over the weekend as there’s a much lower chance that the security command center is being monitored.
Along with attackers using malware to generate ransom demands, we are seeing a wide range of methods being used to disrupt our customers. Some attacks involve brute force password attacks and there’s a growing number of phishing attacks, used to gain access to credentials or hijack payments to legitimate suppliers. It is important for organizations to take a proactive approach to cyber attacks to prevent or at least minimize these encounters before irreparable damage is done.
“Prevention is Better than Cure….”
…As the old adage goes and never was it more applicable than with cyber attacks. In an effort to prevent data breaches and attacks, it’s important that organizations assess their environment or hire the help they need to effectively assess their level of risk exposure. To give you more insight, we’ll explain our approach when working with customers to mitigate these risks.
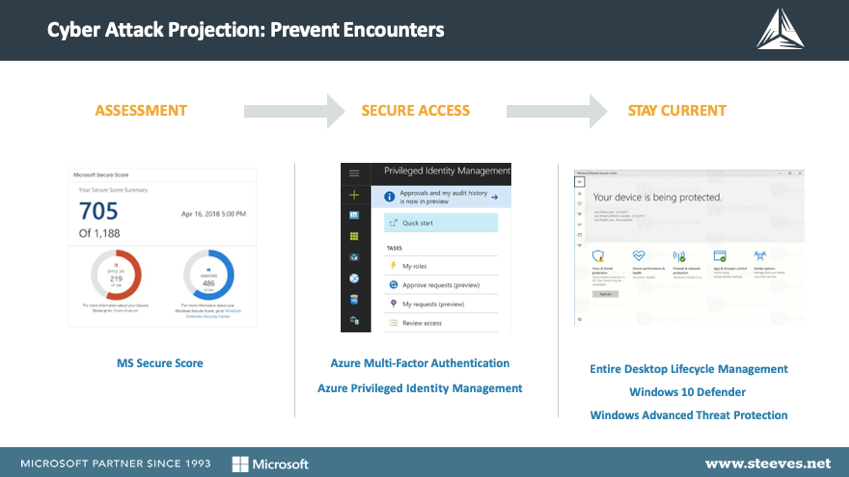
First, we begin with an assessment of the risks and threats to the client environment. We take stock of the clients’ Microsoft Secure Score to obtain a baseline for assessing the highest areas of vulnerability and risk. This step is important as it allows us to prioritize the implementation of tools within the Microsoft 365 suite. This informs our decision on whether to start with Multi-factor Authentication and conditional access or to eliminate passwords altogether with Windows Hello for Business.
When it comes to preventing cyber attacks, we always recommend that clients take advantage of the tools they already have in their arsenal, such as Microsoft 365 and Enterprise Mobility and Security, which are secure, end-to-end solutions that many organizations don’t fully utilize… until it’s too late. These out-of-the-box tools greatly help with preventing a cyber attack and include:
- Windows 10 Defender – enabled by default in Windows 10, this is an anti-malware endpoint device protection solution.
- Windows Defender ATP – allows you to leverage the built-in Windows Defender protection of Windows 10 Enterprise.
- Windows Updates – to consistently keep the OS secured from the most current threats.
How Can We Enable a Modern Workplace while Remaining Compliant?
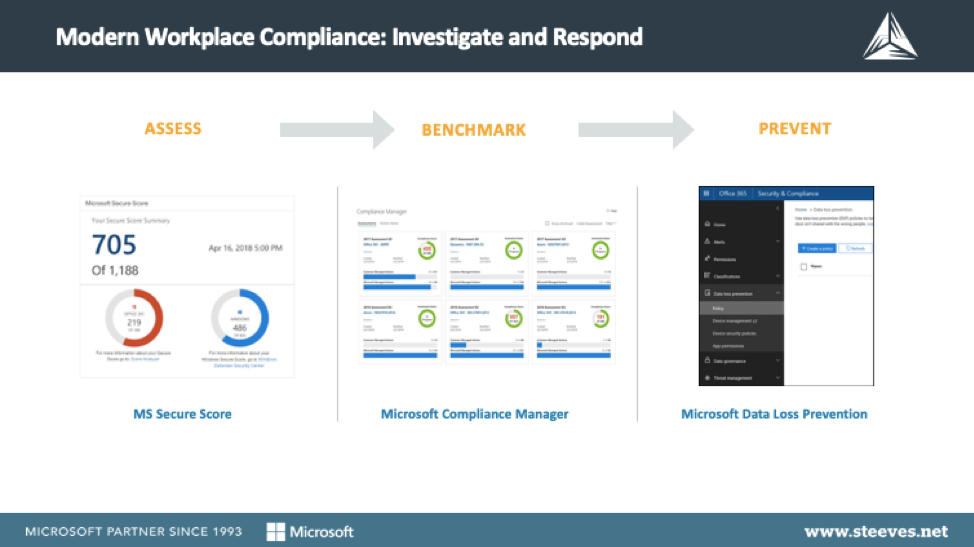
It’s no surprise that enabling a modern workforce, with employees remotely located or regularly on the go can increase an organizations’ exposure to security risks. Large organizations across industries, such as finance, healthcare and the public sector face concerns when it comes to enabling a modern workforce while also remaining compliant, where breaches can have significant legal and financial consequences. Thankfully, Microsoft’s Modern Workplace is equipped with great tools to help organizations with compliance and regulations, such as:
- Microsoft Compliance Manager is great for tracking compliance across multiple compliance regulations and across platforms, including Office 365, Azure and Dynamics 365.
- Microsoft Secure Score can provide organizations with a good benchmark and baseline on where to improve.
- Data Loss Prevention helps to ensure that data such as health and financial records are monitored within documents and users can be warned or blocked from including this type of data in messages sent outside the organization.
- GDPR Assessment helps organizations to measure their compliance with GDPR.
- Office 365 Retention Policies enable organizations to remain compliant when it comes to document retention.
How Can We Empower Remote Workers without Risking Identity Theft?
Organizations can no longer solely rely on a firewall and perimeter security as identity has become the center of how we connect people, devices and data, leaving organizations with a big security challenge. The risk of identity theft is increasing dramatically as we enable employee access through more devices, support remote and mobile workers, and collect more sensitive data. It’s challenging for organizations to secure corporate assets when they’re accessed by users through a variety of devices including personal mobile phones, home computers and business center workstations.
Organizations are understandably keen to experience the benefits of enterprise mobility by providing users with remote access. It’s important that organizations place an emphasis on the risk of identity threats and clearly educate users on how to avoid these threats by following security best practices with strong passwords and not clicking on unknown email attachments or links.
However, organizations cannot rely solely on users to always make the correct decisions when it comes to security protection. Enterprise security best practices need to be enforced to reduce the chance of accounts being compromised by making good use of available technologies such as:
- Conditional Access to enforce MFA, Windows Hello, requiring Password Complexity and expiration.
- Windows Defender ATP to inspect content and restrict untrusted code.
- Provide least-privileged accounts to ensure users can get their job done, without compromising security.
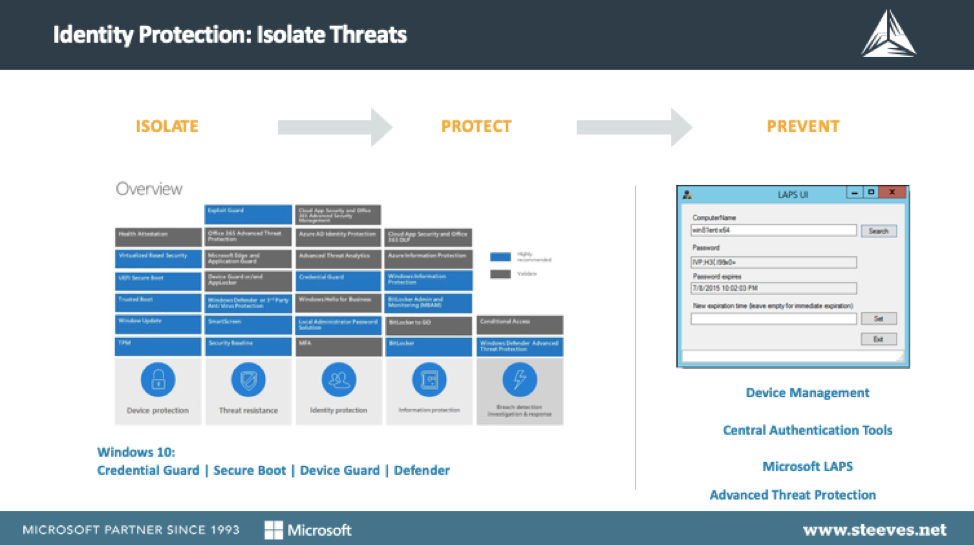
Built-in Windows 10 tools include:
- Credential guard: stops the mining of data in Windows 10.
- Device guard: protects the code secured in Windows 10 to prevent the running of compromised code.
- Secure boot: secures the boot process in Windows 10.
- Windows defender Antivirus: delivers comprehensive, ongoing and real-time protection against software threats like viruses, malware and spyware across email, the web. and more.
A combination of Azure Active Directory, Office 365 and Intune is necessary to secure corporate data on both corporate and personal devices. Compliance policies can be applied to ensure that if a user is going to access corporate resources, certain application and device security expectations are in place.
Another popular enterprise security solution Local Administrator Password Solution, ‘LAPS,’ is used for managing local account passwords of computers on joined domains as it randomizes every devices’ local admin password and is only accessible by authorized administrators. Passwords are securely stored in Active Directory ensuring that only eligible users can read it or request its reset. This free tool from Microsoft is an absolute must for enterprise organizations.
The issue of Identity theft isn’t going anywhere anytime soon so it’s important that organizations employ best practice approaches to isolate threats and reduce exposure with tools such as:
- Central Authentication Tools around Azure Active Directory (AD) – such as Azure AD Password Protection and Smart lockout, Azure AD Single Sign-On for 3rd party SaaS apps reduces the number of accounts and passwords, Multi-factor Authentication for admins.
- Office 365 Advanced Threat Protection – provides the ability to sandbox attachments, URLS and prevent Phishing attacks.
- Privileged Identity Management for administrators.
_____________________________________________________________________________________________________
Interested in Learning more about Enterprise Security & Data Protection?
Watch the Webinar Recording Now, where senior consultants from Steeves and Associates share their knowledge and expertise on what you can do to protect your organization from a costly cyberattack and enterprise security breach.
_________________________________________________________________________________________________________________________
Is it Possible to Enable Collaboration Without Risking a Data Breach?
Many organizations are reaping the benefits of employee collaboration, facilitated through cloud productivity tools but this increases the risk of a potential data breach unless enhanced enterprise security and data protection is implemented.
It’s no longer just about protecting the collaboration tools themselves. Organizations need to think about how employees are using these collaboration tools to access confidential organizational data via personal devices such as phones, tablets and home and business center computers.
Organizations need to ask themselves three questions once organizational data has been sent to a users’ personal device:
- Can you still control who it is forwarded to?
- Can the information be accessed without proper passwords or PINs?
- Can the data be compromised or corrupted on a users’ device by malware or insecure network communications?
It’s challenging to change user behavior but it’s essential that organizations focus on educating end-users on securely managing organizational content when implementing empowering business technologies.
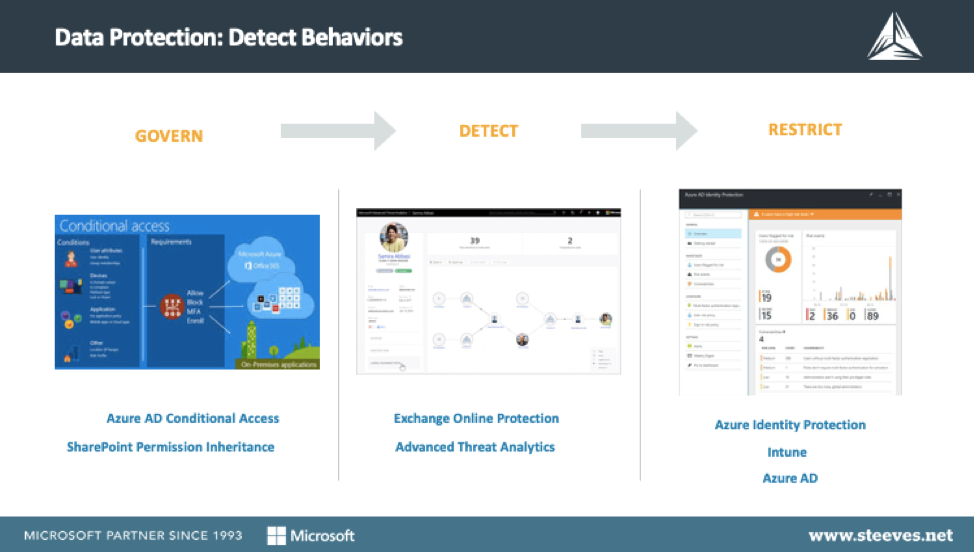
Strong governance and design are an absolute must for organizations that wish to adequately protect themselves. For example, clients with SharePoint environments can lock down highly sensitive data and restrict access to a subset of people.
Azure Active Directory Conditional Access also enables administrators to restrict who employees can share data with. It’s important that organizations conduct data security assessments for all new SharePoint Online builds or when updating existing environments. SharePoint enables permission inheritance and can lock data down further with encryption by utilizing Azure Information Protection. For example, making customer lists unavailable to certain users and/or devices.
Organizations can use Exchange Online Protection to restrict access and/or block a range of IP addresses for attacks they’ve seen coming in. Another great tool that’s useful for quickly detecting threats is Advanced Threat Analytics which helps to identify threats through behavioral analytics and it aids the prioritization of the investigation for remediation when needed.
Azure Active Directory rights management empowers organizations to restrict tasks such as cut and paste between corporate applications and personal applications to provide additional enterprise security, supporting the increase of BYOD (bring your own device) and remote workers. Additionally, organizations can use Active Directory Intune to wipe data from a device after an employee leaves the organization. It can also be efficiently configured so that users lose access to all data when their rights are removed from Active Directory.
How Can Organizations Prevent Intentional and Unintentional Leaks of Confidential Data?
As noted above, 87% of Senior Managers have admitted to accidentally leaking business data. There are a number of ways in which this can occur the most common of which are through –
Phishing Attacks: This occurs when a user responds to an email sent by an imposter impersonating an internal contact or resource, usually requesting financial or other confidential organizational data.
Emailing Confidential Data: This occurs when a user unintentionally includes confidential data such as credit card details or health numbers in an email.
Device Loss / Theft: This occurs when a user loses an unencrypted device such as a USB key or hard drive containing confidential organizational information.
Unfortunately, organizations can experience intentional leaks of confidential information from disgruntled employees. We came across one situation whereby a laid-off employee with administrative access that was actively deleting volumes of business data. Another unfortunate occurrence happened when an employee who was leaving a company had set up a “service account” with administrative and VPN access to enable access to confidential business data after they had left the organization.
There’s an increase in the risk of a data leak when employees have unauthorized or unmonitored administrative access to the organization’s data management. The physical removal of sensitive data through off-site back-ups also increases risk. There are many small organizations whose sole backup strategy consists of one person backing up the data and taking it home with them on a weekly basis, this is definitely not a secure approach to preventing a data leak.
Enhanced Enterprise Security & Data Protection Features & Tools
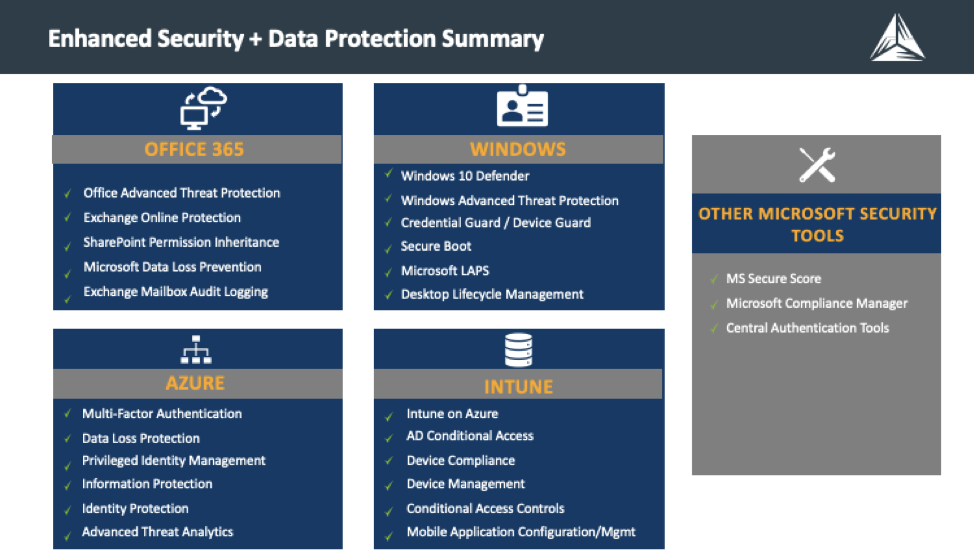
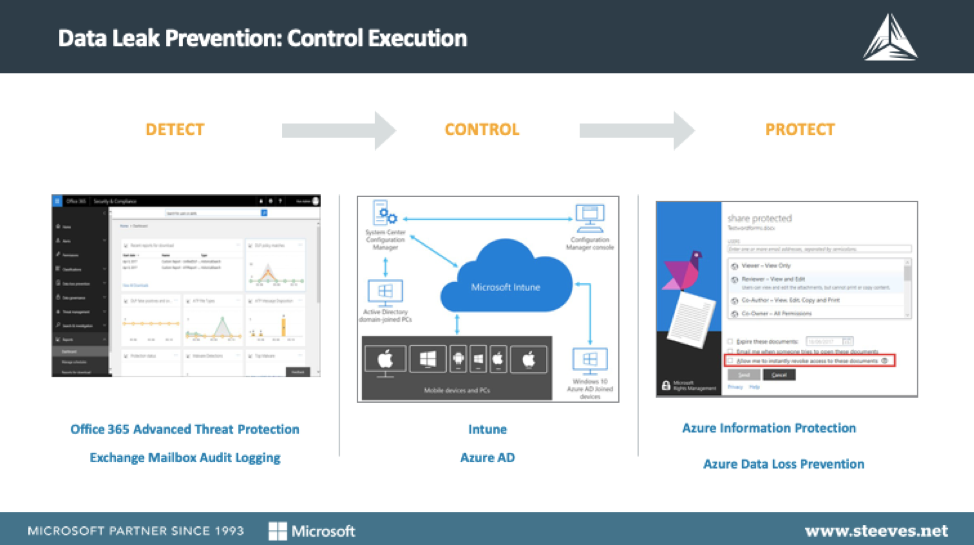
Many organizations are already utilizing Office 365 but may not be taking advantage of its available enterprise security and data protection features including:
- Office Advanced Threat Protection – (ATP) safeguards your organization against malicious threats posed by email messages, links (URLs) and collaboration tools.
- Exchange Online Protection – anti-malware and anti-spam filtering to protect mailboxes and data loss prevention capabilities to prevent users from mistakenly sending sensitive information to unauthorized people.
- SharePoint Permission Inheritance – Permission inheritance enables an administrator to assign permission levels at one time, and have the permissions apply throughout the site collection.
- Microsoft Data Loss Prevention – Identify sensitive information across many locations (SharePoint online, OneDrive for Business & Teams) and prevent the accidental sharing of sensitive information.
- Exchange Mailbox Audit Logging – track who logs on to the mailboxes in your organization and what actions are taken including logs of mailbox access by users other than the mailbox owner.
Windows enterprise security and data protection features include:
- Windows Defender Antivirus – delivers comprehensive, real-time protection against software threats like malware, viruses and spyware across email, applications, the cloud and the internet.
- Windows Advanced Threat Protection – a platform designed to help enterprise networks prevent, detect, investigate, and respond to advanced data security threats.
- Credential Guard / Device Guard – uses virtualization-based security to isolate highly confidential data so that only privileged system software can access them.
- Secure Boot – a security standard to help ensure that a device boots using only software that is trusted by the Original Equipment Manufacturer (OEM).
- Microsoft LAPS – provides management of local account passwords of domain-joined computers.
Azure enterprise security and data protection features include:
- Multi-Factor Authentication– helps safeguard access to data and applications, with additional authentication, while maintaining simplicity for users.
- Data Loss Protection – enables organizations to identify, monitor, and automatically protect sensitive information across Office 365.
- Privileged Identity Management – enables organizations to limit administrator access to privileged roles, discover who has access, and review privileged access.
- Information Protection – enables organizations to control and help secure email, documents, and sensitive data that are shared outside of the company.
- Identity Protection – Detect potential vulnerabilities affecting organizational identities and configure conditional access policies to automatically respond to suspicious actions.
- Advanced Threat Analytics – Review the timeline of a security attack for a clear and convenient view of suspicious activity or persistent threats.
Intune enterprise security and data protection features include:
- Intune on Azure – enables productivity across the workforce while also protecting corporate data.
- AD Conditional Access – control how authorized users access cloud apps.
- Device Compliance – review device compliance and troubleshoot compliance-related issues.
- Device Management – ensure that managed devices are providing the resources that users need while protecting that data from risk.
- Conditional Access Controls – block access altogether or allow access with additional requirements.
- Mobile Application Configuration/Mgmt – manage the client apps that your company’s workforce uses.
With organizations reaping the rewards and productivity gains of technology it’s important that more emphasis is placed on protecting organizational data and infrastructures to avoid the devastating, costly and sometimes irrevocable implications of cyber attacks and enterprise security breaches.
If you would like to learn more about protecting your organizational infrastructure and data from a cyber attack, contact us today at + 1 888 952 8800 or email info@steeves.net.
Author: Dave Steeves
 Dave Steeves, CEO and Founder of Steeves and Associates, has been on the cutting edge of technology throughout his career with the past 25 years running his own company as Microsoft 1st Canadian Cloud Partner and one of the first Microsoft Certified Partners. Steeves has always been an early adopter and visionary, helping his clients adopt disruptive emerging technologies managing risk with careful selection of viable use cases to create value. When not tinkering in tech Dave enjoys hockey, skiing, and spending time with his family.
Dave Steeves, CEO and Founder of Steeves and Associates, has been on the cutting edge of technology throughout his career with the past 25 years running his own company as Microsoft 1st Canadian Cloud Partner and one of the first Microsoft Certified Partners. Steeves has always been an early adopter and visionary, helping his clients adopt disruptive emerging technologies managing risk with careful selection of viable use cases to create value. When not tinkering in tech Dave enjoys hockey, skiing, and spending time with his family.