Windows 10 Quick Assist: Helpful Remote Assistance App or Potential Vulnerability?
At last month’s Endpoint Management Summit, one of the speakers, Jörgen Nilsson, asked the room full of Enterprise Administrators how many had heard of a Windows 10 feature called ‘Quick Assist’. Only a couple of hands raised. Considering the security and privacy implications of this feature for most enterprises, it is absolutely a tool that every administrator should be aware of.
What is Windows 10 Quick Assist?
A built-in feature of Windows 10, Quick Assist is a remote assistance tool. In a nutshell, Windows 10 Quick Assist allows you to view or control another user’s computer. All you need is a Microsoft account, such as Hotmail or Outlook.com. It is important to note that, the user requesting help via Quick Assist does not need a Microsoft account to get help via Quick Assist.
With the number of remote workers today, Quick Assist can seem like an ideal solution for fast and simple troubleshooting, regardless of each employee’s location. Quick Assist can enable users to get Windows 10 support when there is no other mechanism available.
How Does Windows 10 Quick Assist Work?
For example, let’s say an employee/user on your network wants to share their desktop to get assistance from someone outside your organization. The user and their “emergency IT tech” both open the Quick Assist application on their Windows 10 computers. The “emergency IT tech”, who may NOT be affiliated with your help desk or even one of your corporate users, selects assist another person and a six-digit code will be generated on his/her computer. The employee/user then enters this code into the Quick Assist on the other Windows 10 computer. That’s it! A connection is created and the Quick Assist remote help session is established, providing access to your internal network via that employee/user’s machine.
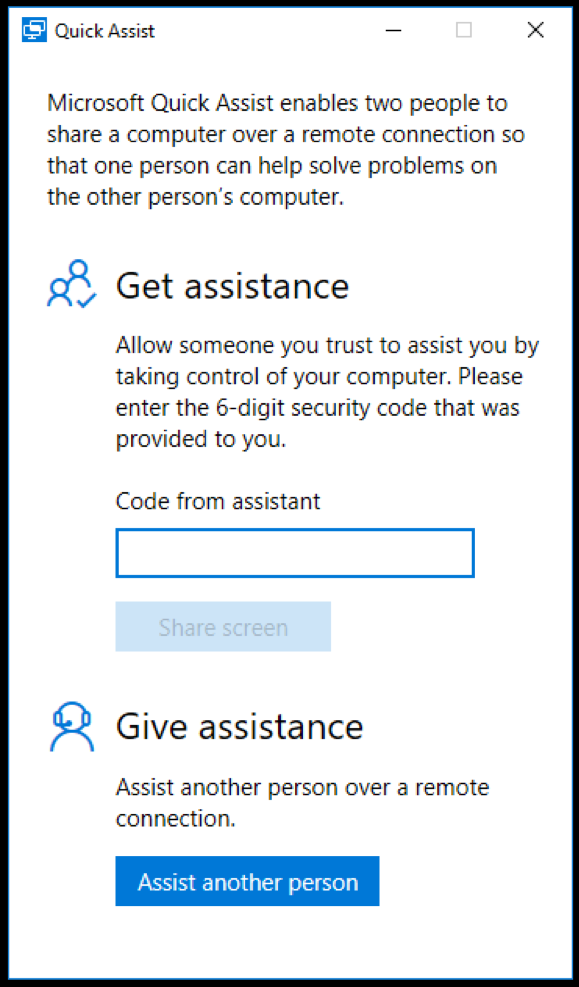
Should My Organization Use Windows 10 Quick Assist?
Quick Assist can be a great tool to ensure that minor technical issues don’t slow down your team’s productivity. Natively, it is built-in to every Windows 10 computer and is on by default, making it simple to use. Having said that, this brings use to some concerns from a privacy and security standpoint.
Few people are aware of this, but Windows 10 has had a built-in remote assistance feature, enabled by default, since Windows 10 v. 1607. With the more recent addition of Quick Assist, this feature is getting simpler to use – and unfortunately, exploit.
Fortunately, most users (and administrators) are unaware of this feature change to Windows 10, but anyone who knows can simply search for Quick Assist from their start menu and access the tool.
However, it is likely that those who do know about the feature are probably the exact users you, as the administrator, really would rather not use it. For instance, a hacker posing as a Microsoft Security specialist contacts your unsuspecting user and tells them “we have detected that your computer has a virus and needs to be cleaned”. Of course, your unsuspecting user follows the instructions, enters the six digit access code, and the hacker is in.
Does Quick Assist Leave Your Enterprise Exposed?
The quick answer is YES. Thus far, Quick Assist is not well documented, and in my opinion, presents several major security concerns for Windows 10 users:
- No group policy settings option to control – essentially, you cannot set limits on who uses Quick Assist to receive help – or, more concerning – who provides the help.
- Most firewalls & NAT will be bypassed – Quick Assist connects to a central Microsoft support server using the port 443 (for both sides of the assist connections), as such this will bypass most existing firewalls and NAT.
- No login or user credentials – neither the assister or assisted are required to login or validate credentials to use Quick Assist, which means there is no way to know who accessed the computer, from where, or what was done.
Can I Block or Remove Quick Assist in Windows 10?
Every enterprise should carefully consider the privacy and security implications of this default Windows 10 feature. Every corporate IT Security administrator should prioritize developing a plan to either control and manage Quick Assist or to remove access to Quick Assist in Windows 10.
Should you chose to remove Quick Assist from your Windows 10 machines, you have the following options:
- Quick Assist Revoke Access from a Single Computer: You can remove Quick Assist on each computer individually by using the Manage Optional Features within the Windows 10 settings page and simple remove access.
- Quick Assist Revoke Access for Multiple Computers: You can also revoke access to Quick Assist with a PowerShell script, which makes a lot more sense if you are remediating multiple computers. The script needs to contain the following command: Remove-WindowsCapability -online -name App.Support.QuickAssist~~~~0.0.1.0
- Block Quick Assist Access via Firewall: Another computer-level solution is to block Quick Assist via firewall. Quick Assist is an executable, which is found at %windir%\system32\quickassist.exe. By creating a Windows Firewall or Applocker rule blocking access of that executable to the internet, you effectively block Quick Assist.
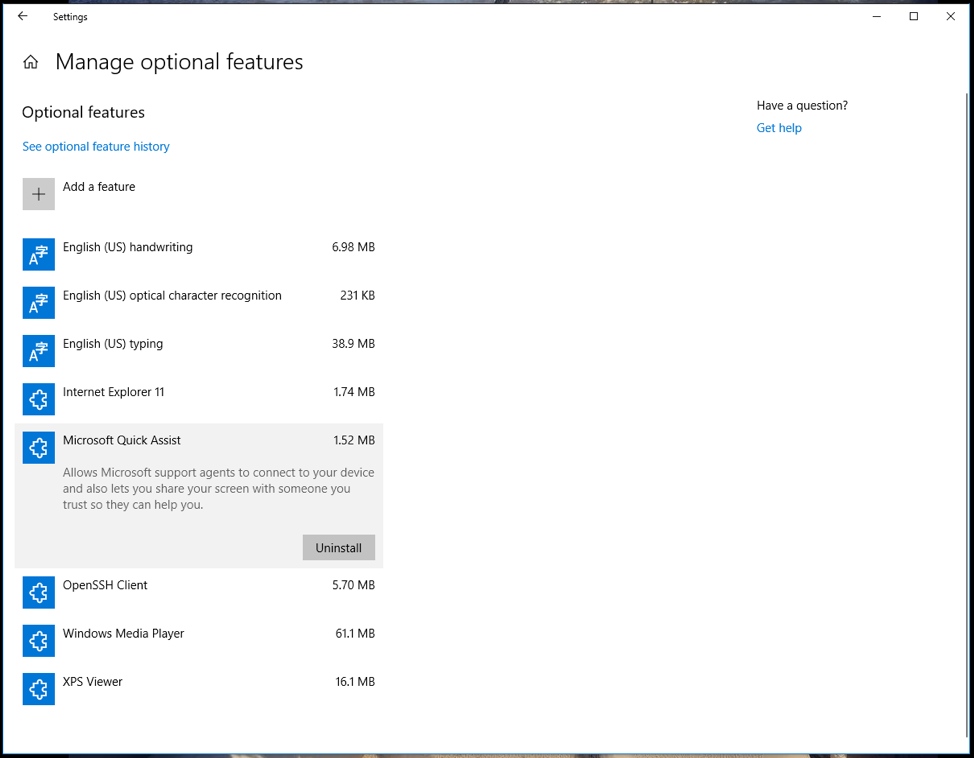
Is Quick Assist a Fast Win or Quick Loss?
While Quick Assist seems to provide a valuable feature for Windows 10 users, some argue that the functionality is better suited to use by individuals as opposed to enterprise organizations. Ultimately, how you decide to deal with Quick Assist will depend on compliance, governance and security policies. Quick Assist can be used as a nice remote support tool, but should be carefully planned, managed and controlled, or removed if you don’t intend to use it.
If you still have questions about Quick Assist in Windows 10, feel free to reach out – 1 888 952 8800 or info@steeves.net. We’d be happy to help!
Author: Doug Griffin
 Doug Griffin is an experienced Endpoint Management & Mobility Architect at Steeves and Associates. With a focus on System Center Configuration Manager since 1998 as well as Microsoft InTune, there are few in the field that has more hands-on experience. Doug Griffin also holds a wealth of certifications from Microsoft, including MCSA, MCTS, MCITP and is a Microsoft Certified Trainer. Griffin also has a Bachelors of Science from the University of Saskatchewan and over a decade of experience as an MCT, providing classroom and online based training in SCCM and other Microsoft products. In his time off, Doug enjoys playing Squash, although after years of practice he is still not very good at it.
Doug Griffin is an experienced Endpoint Management & Mobility Architect at Steeves and Associates. With a focus on System Center Configuration Manager since 1998 as well as Microsoft InTune, there are few in the field that has more hands-on experience. Doug Griffin also holds a wealth of certifications from Microsoft, including MCSA, MCTS, MCITP and is a Microsoft Certified Trainer. Griffin also has a Bachelors of Science from the University of Saskatchewan and over a decade of experience as an MCT, providing classroom and online based training in SCCM and other Microsoft products. In his time off, Doug enjoys playing Squash, although after years of practice he is still not very good at it.

