Is Microsoft Defender for Endpoint Worth All the Hype?
We know that endpoint security is a huge part of organizations, especially if there are users and members working remotely or accessing documents and data from multiple devices. Microsoft Defender for Endpoint is a comprehensive solution for endpoint protection. Defender for Endpoint is an enterprise endpoint security product that supports Mac, Linux, and Windows operating systems, along with Android and iOS The platform has been curated to help enterprise networks prevent, detect, investigate as well as respond to threats for end-user devices such as tablets, cellphone, laptops, servers and more.
Where does Microsoft Defender for Endpoint Fit In?
Formerly known as Microsoft Defender Advanced Threat Protection, Microsoft Defender for Endpoint is based in the cloud and requires no additional hardware or software deployment, or infrastructure while also supporting auto-updates. Thus, it leaves your endpoints protected and updated at all times. If your organization is on the lookout for an effective endpoint protection tool, one backed by Microsoft security experts – Microsoft Defender is definitely the one to consider.
Microsoft Defender for Endpoint is a key component of the Microsoft 365 security suite which involves other Microsoft security solutions such as Microsoft Defender for Identity, Microsoft Defender for Office 365, and Microsoft Cloud App Security.
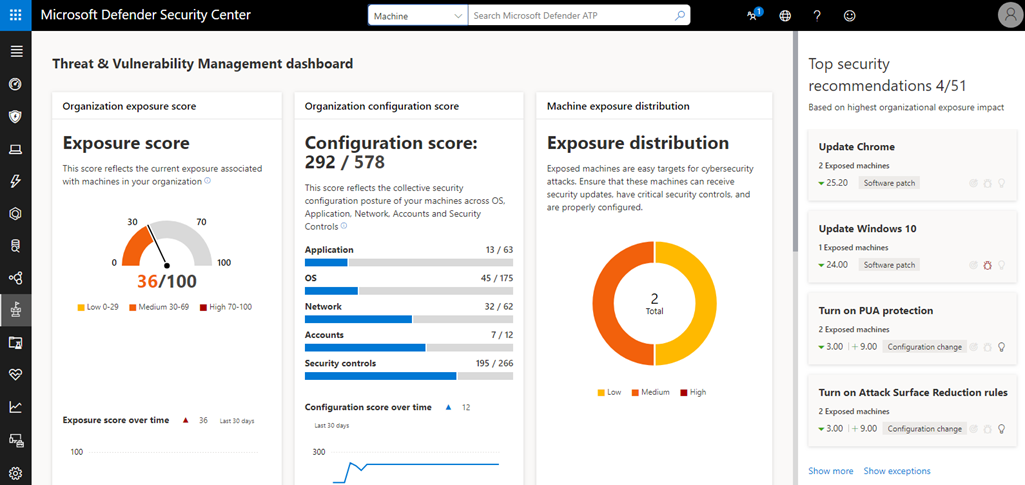
Built on Azure cloud, every customer gets a dedicated Microsoft Defender for Endpoint tenant, each isolated from every other tenant. That means organizational data is isolated and secured within the customer’s tenant and that data is only accessible by customers through Azure Active Directory Authentication. Security teams use the Microsoft Defender Security Center to access their Defender for Endpoint data and to interact with endpoints.
The 7 Pillars of Defender for Endpoint
What makes Microsoft Defender for endpoint so powerful? It is the 7 pillars of security that set it apart from other endpoint protection tools. Its core features provide preventative protection, post-breach detection, automated investigation, and responses to possible breaches in endpoint security. Explore the seven advanced capabilities of Defender for Endpoint below:
- Threat and Vulnerability Management: A healthy security program involves the ability to identify assess and remediate weaknesses. Defender for Endpoint does exactly that by discovering the loopholes, weak points, and any misconfigurations in real-time. The Threat and Vulnerability Management feature uses a risk-based approach to discover and prioritize detected threats. What makes this capability so powerful is that it can help bridge the gap between security operations, Security Administration, and ID administration.
- Attack Surface Protection: The main reason organizations choose Microsoft Defender for Endpoint is simply to reduce cyber security risks. Attack Surface Protection is at the front line of defense in the stack. The Attack Surface Protection features not only include network protection and web protection but also application control, exploit protection, network firewall, and controlled folder access. Through this, endpoints are able to mitigate risk and resist attacks and exploitation as its settings help regulate access to malicious IP addresses, domains, and URLs.
- Next-Generation Protection: This capability has been specifically designed to catch all types of emerging threats that enable you to further strengthen the security perimeter of your network. With elements like machine learning, big data analysis, and threat resistance research, Next Generation Protection in Windows acts as real-time antivirus protection.
- Endpoint Detection and Response: These features have been designed to detect, investigate, and respond to advanced threats that have somehow made it past the ‘Threat and Vulnerability Management’ features and the ‘Attack Surface Reduction’ capabilities. With a query-based threat hunting tool, advanced hunting lets you proactively find breaches and create custom detections. With the behavioral cyber telemetry gathered by Defender for Endpoint, analysts are able to go back in time to the start of the attack and plan a course of action to safely move forward.
- Automated Investigation and Remediation: Security alerts can be flooding your organization’s environment and overwhelm ng security teams at a rapid rate. However, the Automatic Investigation and Remediation features help reduce the volume of alerts and increase the overall response time.
- Microsoft Secure Score for Devices: One of the best ways to detect the security state of your enterprise network is through a security score. Defender for Endpoint helps organizations to dynamically assess the current state of security by providing a high-level view of its device configuration. It helps identify any unprotected systems to improve the overall security of your organization. The Security Score provides recommended actions to improve and strategize a better security plan.
- Microsoft Threat Experts: A great capability that further empowers security operation centers to identify and respond to threats quickly as well as accurately is the all-new managed threat hunting service. This is a method that ensures proactive hunting prioritization while providing additional context and insights. It’s important to remember that Defender for Endpoint customers must apply for Targeted Attack Notifications in order to obtain insights and analysis on the most critical organizational threats to ensure your team can quickly respond.
How Does Defender for Endpoint Protect Organizations?
Defender for Endpoint is based on a combination of technology that is built into Windows 10 and Microsoft’s robust cloud service. With the expertise of over 3500 security experts from around the world, Microsoft has put together something truly remarkable. Organizations can utilize integrated workflows to onboard and secure devices while increasing the productivity, efficiency, and safety of the environment. Let’s take a look at how Defender for Endpoint is able to follow through on its security goals:
- Endpoint Behavioural Science: By collecting and processing behavioral signals from the Windows operating system the embedded sensors send data to a private isolated cloud instance of Microsoft Defender for Endpoint.
- Cloud Security Analytics: Across the Windows ecosystem, Microsoft leverages device-learning and big-data optics to translate behavioral signals into insights, detections, and even recommended responses to advanced threats faced by devices.
- Threat Intelligence: Defender for Endpoint can identify attacker tools, techniques, and procedures, and generate alerts based on threat intelligence data generated by Microsoft security teams.
Defender for Endpoint provides advanced threat protection that includes antivirus, antimalware, ransomware mitigation, and more, along with centralized management and reporting.
With the added ability to discover and secure unmanaged endpoints and network devices, Defender for Endpoint delivers protection to hybrid settings as well. Just as easily, once the network devices are discovered, security administrators will receive the latest security vulnerabilities and recommendations on them.
Moreover, Defender for Endpoint involves features that enhance the antivirus protection already installed on your endpoint. Take advantage of using Microsoft Defender Antivirus alongside any other non-Microsoft antivirus solution in your environment. In this scenario, the Microsoft Defender Antivirus will run in passive mode while the other solution runs as the primary if the following requirements are met:
- The operating system must be one of Windows 10 or newer; Windows Server 2022, Windows Server 2019, or Windows Server, version 1803, or newer
- Endpoints must be onboarded to Defender for Endpoint
Endpoint for Defender also has a detonation chamber in organizational tenants for deep-file analysis. It acts as a sandbox where security teams can upload suspicious files and get a readable report. This is an incredibly powerful yet safe way to investigate potential threats.
Reduce Alert-to-Action Time
It is likely that your organization’s system will receive multiple alerts in a short period of time. But there is so much more to your one-stop solution, Defender for Endpoint then meets the eye. The automated investigation response capability of Microsoft Defender for Endpoint allows you to keep things simple and respond quickly and correctly to incoming threats. With the help of various inspection algorithms to discover malicious activities on a device, the automated investigation response provides remediation practices automatically. Not only does this reduce the volume of incoming alerts but it also allows your security teams and operations to focus their attention on high-value tasks. By providing security teams with a course of action to tackle threats, complex threats can be remediated within minutes, saving valuable time and providing the peace of mind of a secure network.
Get Your Hands on Defender for Endpoint
Very soon, two plans will be available to access Defender for Endpoint:
Plan 1 is currently in preview and will include next-generation protection, attack surface reduction, manual response actions, centralized management, security reports, and APIs that allow you to integrate it into your existing workflows.
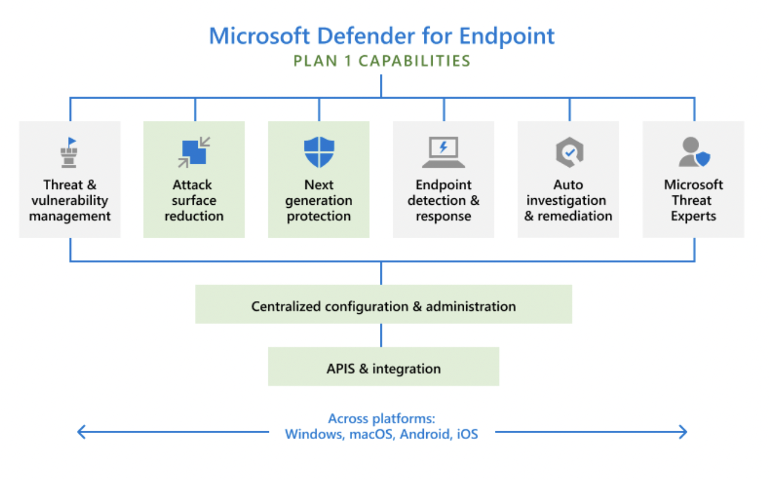
Plan 2 is generally available, includes the complete Defender for Endpoint Plan 1 plus the additional capabilities of device discovery, threat and vulnerability management, automated investigation and response, advanced threat hunting, point detection and response, and access to Microsoft threat experts.
Does Defender for Endpoint Have What It Takes?
Microsoft Defender for Endpoint is not just a party-trick but a holistic platform with innovative functionalities and an integrated experience that meets your cybersecurity needs. First, the main benefit you get is the robust way that all your endpoints are secure and by extension, your network is protected from cyber-attacks.
We have already iterated its proactive approach to security that minimizes entry points for breaches. Defender for Endpoint places your devices in the best security posture possible by blocking and alerting against untrusted applications and websites. In the event that a suspicious activity occurs, Microsoft Defender for Endpoint reviews the threat and takes action without the need for an IT team member to be available then and there.
It also provides a rich understanding to your security team by giving them full visibility of your organization’s environment through an informative dashboard.
There is nothing as powerful as analytics-based, cloud-powered, post-breach detection. Not only does Defender for Endpoint quickly adapt to evolving threats, but it also makes use of advanced analytics and big data. It is further strengthened by the Intelligent Security Graph with signals across Windows, Azure, and Office to detect unknown threats, providing actionable alerts that enable your security team to respond quickly.
As mentioned among the pillars of Defender for Endpoint, threat intelligence is key to identifying breaches. Defender for Endpoint generates alerts when it identifies attacker tools, techniques, and procedures based on data generated by Microsoft threat hunters and security teams, augmented by intelligence provided by Microsoft Partners.
Are you ready to explore the best security strategy for your organization? We can provide you with a complete Microsoft Security Assessment and determine the best Defender for Endpoint plan for your organization. Steeves and Associates is here to empower you with an integrated threat protection strategy, get in touch for more details.

