How to Plan & Implement Microsoft 365 Security [A TRU Higher Education Case Study]
Many organizations, including Higher Education institutions, often find it challenging to keep up with the number of portals in Microsoft 365 Security given how fast the security landscape and the portals themselves change. Throughout this article, we will help you identify the different tools that are available in the Microsoft 365 Security suite and explore the optimal approach to securing your environment.
Getting Started with Cybersecurity
If you are just getting started with cloud security, then the first thing you need to do is acquaint yourself with the different cybersecurity products in the Microsoft 365 security center. There are many different products available, and each has features and configurations that enable organizations to secure their cloud environments, we’ll dive into this a little later.
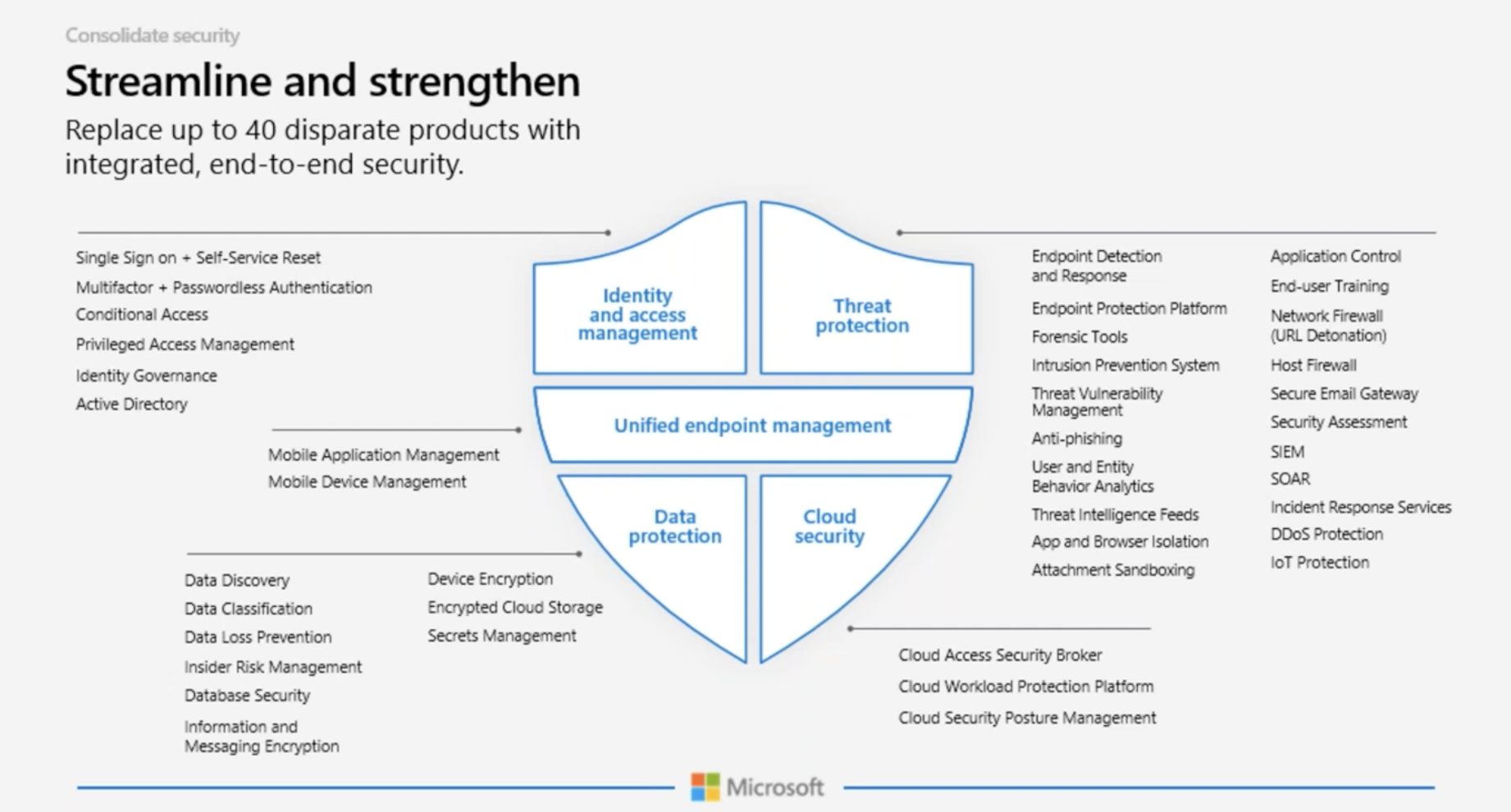
With the plethora of technologies available, it can be hard to decipher which solution to deploy if you have limited time and resources. Therefore, you need the necessary information to prioritize and plan which solutions will best secure your environment and improve your overall security posture.
Strategizing Your Microsoft 365 Security Architecture
This is where a Maturity Model comes in handy, and you can utilize Microsoft’s ad hoc dynamic security model in their security center (now known as Microsoft 365 Defender) to get a better understanding of your security needs.
Microsoft 365 Defender gives you an insight into all the security components in the Microsoft 365 security suite. We recommend that you check your organization’s Microsoft Secure Score as a first step in devising your organization’s cloud security strategy.
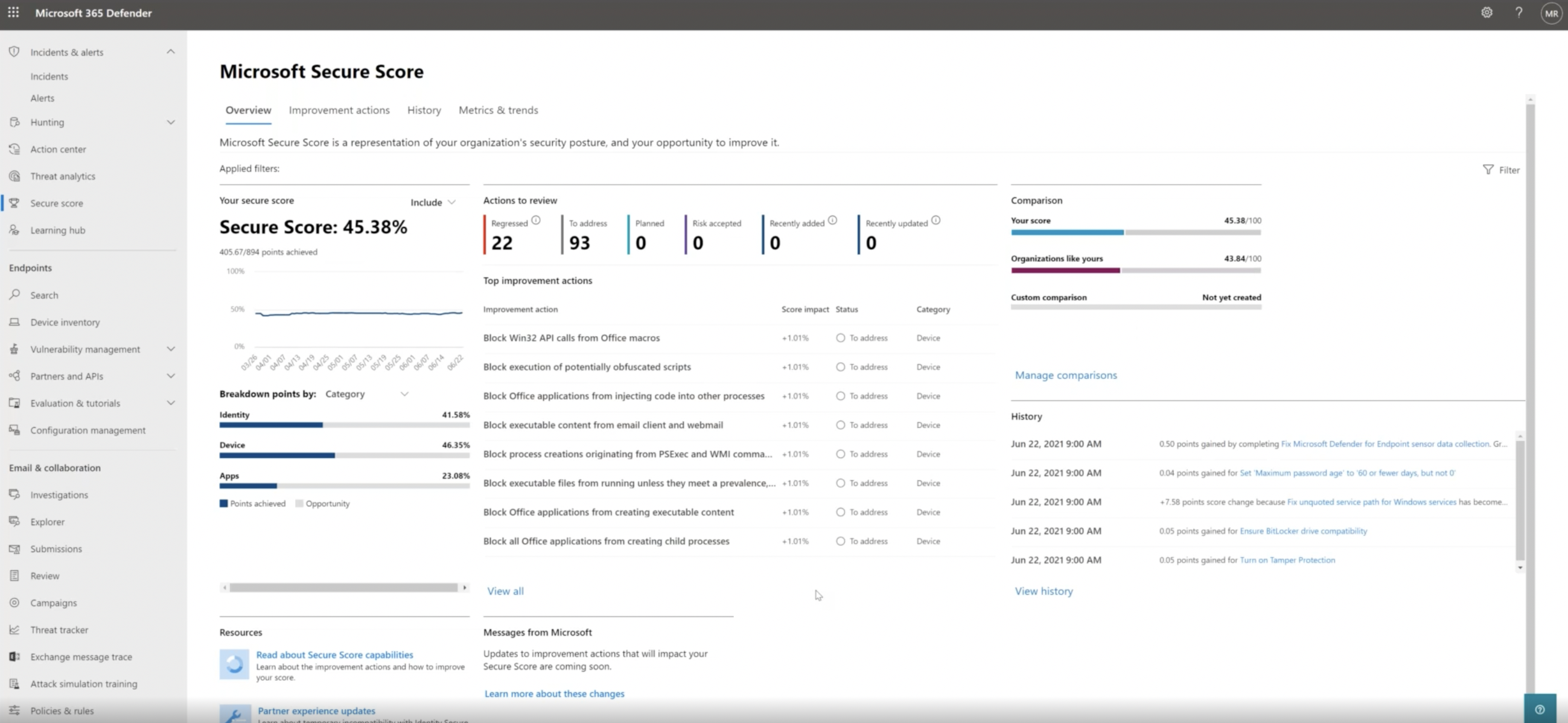
The image above displays a rollup of secure scores such as endpoint secure score and identity secure score among others. It allows you to judge your organization in terms of cloud security maturity while also providing a comparison to other similar organizations.
As we can see in the image above, this tool provides useful insights such as improvement actions and history that show what actionable steps can be taken now and it also helps to inform how your security position evolves over time.
By looking at the top score impacts you will be able to determine the critical areas that require improvement and by drilling down into specific components you can view details of the exact changes that need to be made and how these would impact your Microsoft Secure Score.
Thompson Rivers University: Cloud Security Case Study
Thompson Rivers University (TRU) has been around for over 50 years and currently serves over 25,000 students across its campuses and via Open Learning Programs. The University’s Information Security Program started in 2007 and had achieved a significant level of maturity by last year.
With the onset of the pandemic, and the shift to remote work, TRU adopted Microsoft Teams and SharePoint, and as a result, the information stored in their cloud environment grew exponentially. It was at this point that TRU got involved with Steeves’ Security Workshops.
From here on, Steeves and Associates conducted sessions to work through the Microsoft 365 Security Center with TRU, helping the team to get oriented with Microsoft’s cloud security capabilities and to strategize on the best approach to secure TRU’s cloud environment.
With the growing expanse of cloud solutions, TRU needed guidance on developing a robust cloud security strategy along with help to understand Microsoft’s broad cloud security offerings. The provision of up-to-date training on Microsoft Security Solutions was integral for bridging the knowledge gap and supporting personnel changes at TRU.
TRU’s Cloud Security requirements included the need for:
- Visibility across the cloud services they were already using
- Multi-factor authentication going outside of the TRU campus
- Reliable security policies to detect threats without overwhelming the staff with unnecessary alerts
- Enhanced compliance and risk management
- Expert insights on the optimal cybersecurity configuration
Steeves and Associates continue to work with TRU to provide guidance as needed so that the University can continuously improve its overall cloud security posture.
Watch the On-Demand Webinar to Learn More About Microsoft Cloud Security!
Check out the on-demand webinar now for an overview of Microsoft Cloud Security, including a live demonstration of MCAS, Azure Sentinel, Microsoft 365 Defender, and Threat Hunting!
Cloud Security Insights and Visibility
To achieve good visibility into your cloud applications, you need to make use of a Cloud Access Security Broker (CASB) and the Microsoft product for this is called ‘Microsoft Cloud App Security’ (MCAS). Microsoft Cloud App Security integrates with Office 365 and its applications along with third-party apps like DropBox and it uses an API to monitor applications in real-time. With the Office 365 A3 license, you get access to Office 365 monitoring but in order to monitor non-Microsoft components as well, you need an Office 365 A5 license.
The most useful section in MCAS is this Discovery Dashboard. If you integrate MCAS with your endpoints and firewall logs, it will display cloud metrics from the different applications that users are using.
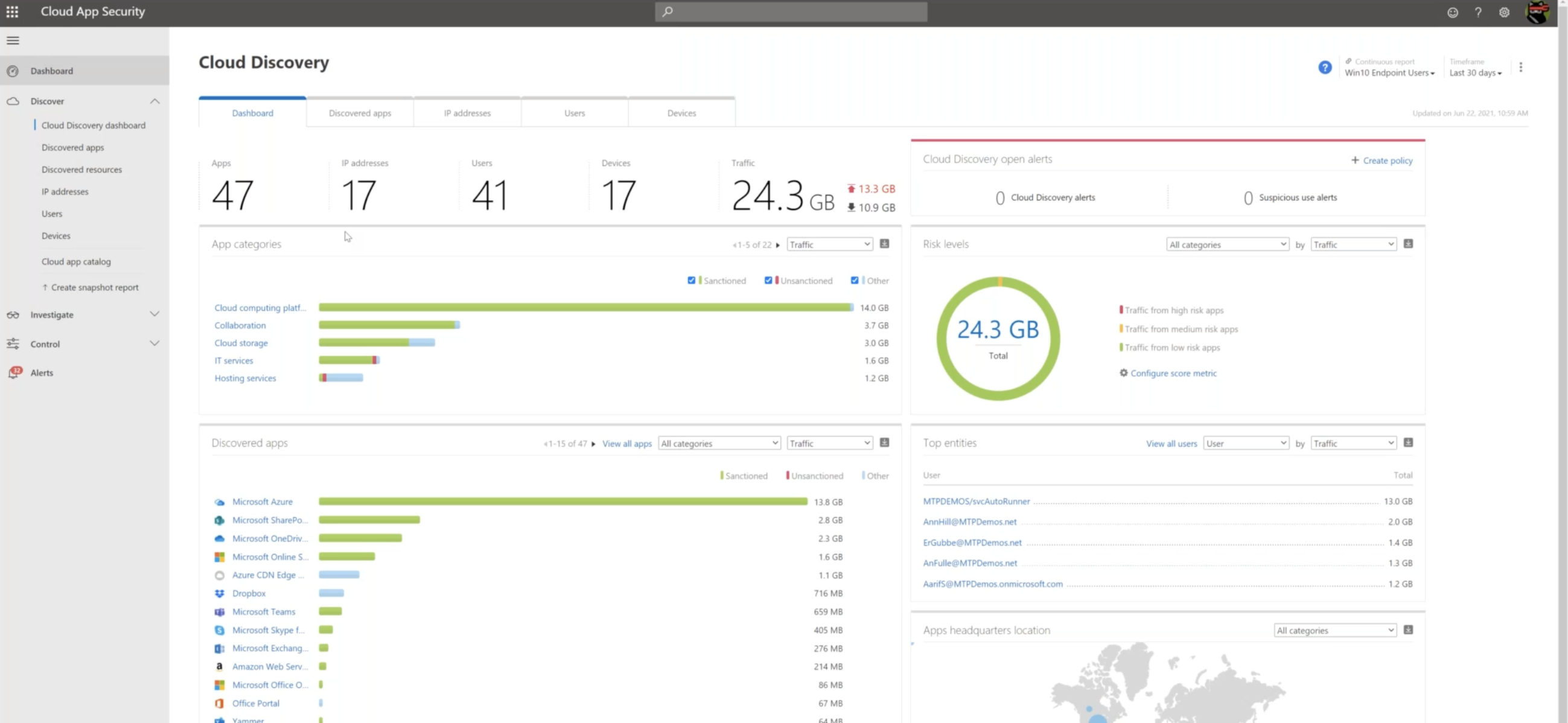
Another powerful tool in Cloud App Security relates to alerting. Looking for anomalous and potentially malicious activities, MCAS creates alerts around such issues based on heuristics.
These alerts are extremely useful for highlighting potential threats to your cloud environment.
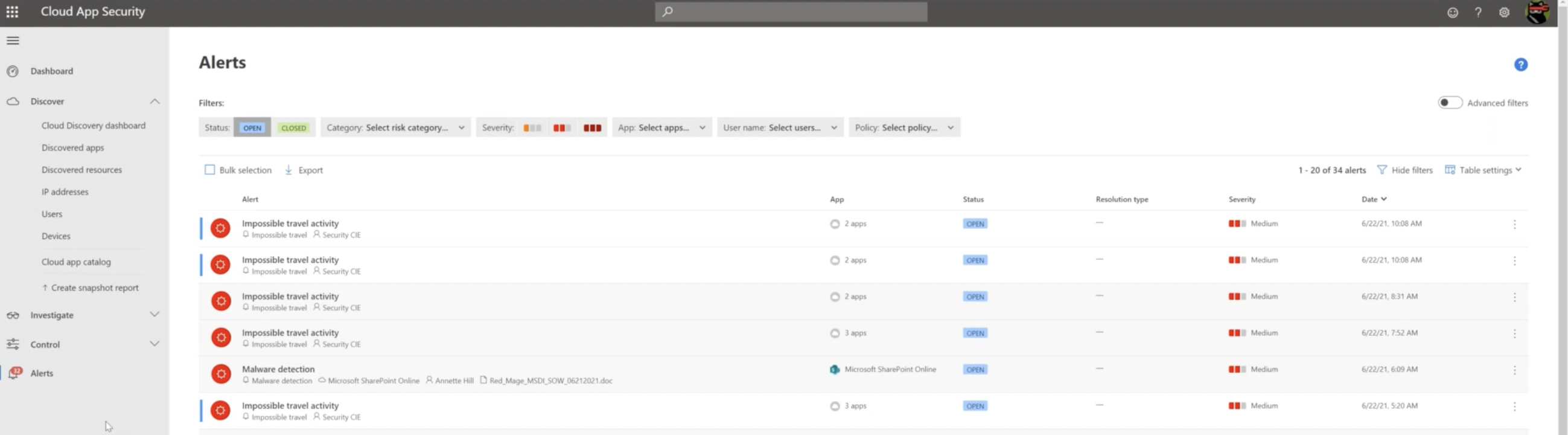
There are policies available in MCAS out-of-the-box that trigger these alerts, but there is also the option of configuring built-in templates to ensure that the alerts better match the needs of your organization. Authorized users can fine-tune alerts based on specific apps and users as required.
A noteworthy feature to mention is that Microsoft Cloud App Security leverages the APIs provided by the cloud provider such as Azure, AWS, and Google Cloud Platform, to enable greater visibility and control by MCAS over the apps you connect to.
Assessing Threat Exposure
After implementing Microsoft Cloud App Security, it is important to familiarize yourself with the attacks and threats that your organization faces. . These will be unique based on your organizational risks and attack vectors. The MITRE ATT&CK Framework is a resource that helps cybersecurity analysts focus on the most likely areas of exposure and out how to prevent cyber-attacks in their different stages.
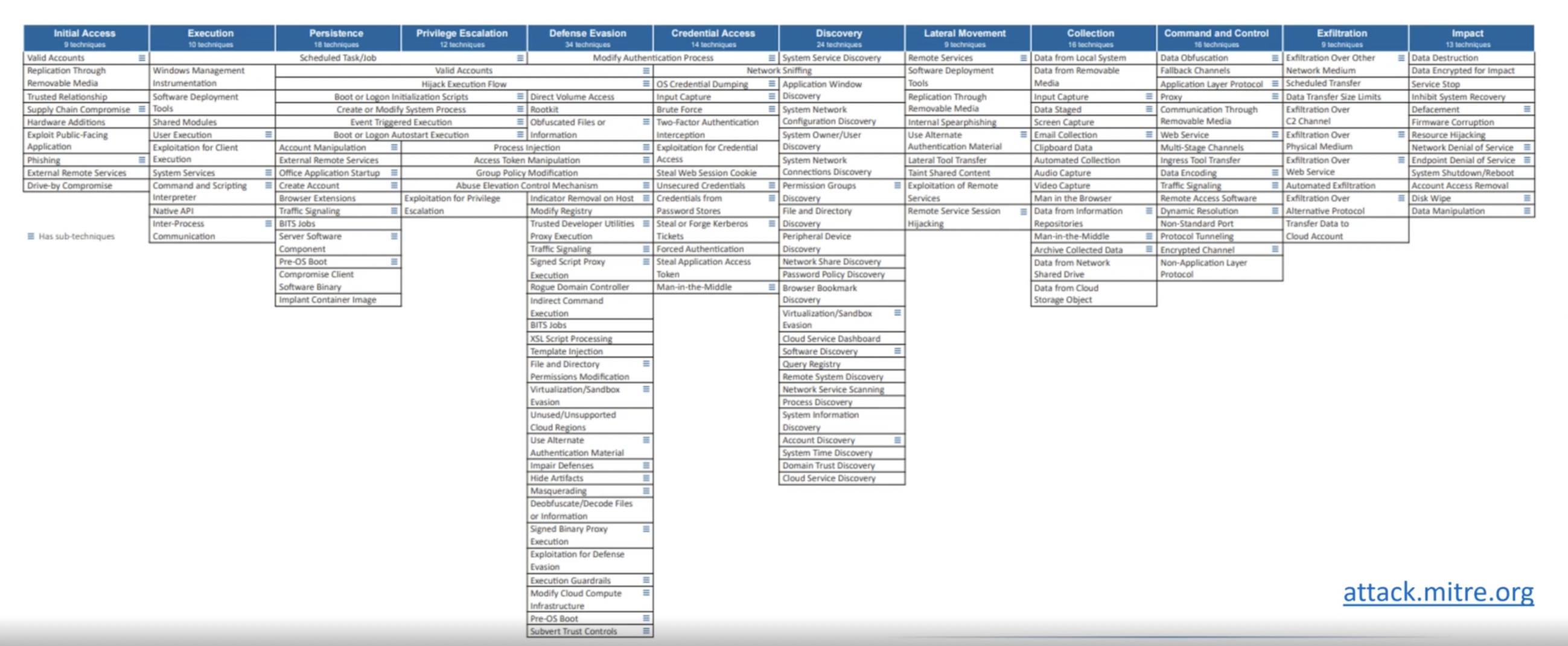
MICROSOFT 365 DEFENDER
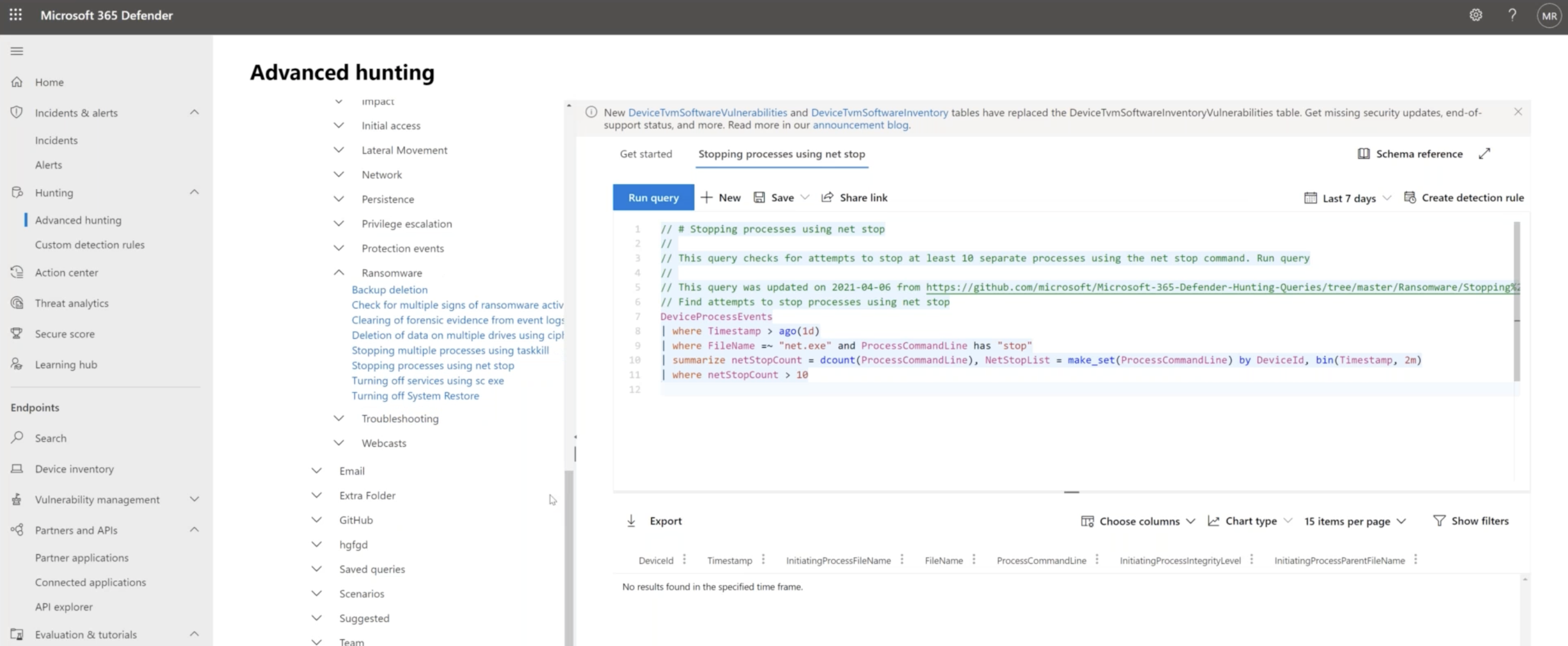
The MITRE ATT&CK Framework is a good resource to use for the threat hunting component of Microsoft 365 Defender. In the Advanced Hunting window, you can do specific searches based on the MITRE ATT&CK Framework or based on community queries or your own queries to assess potential security threat activities, such as potential activities associated with a Ransomware attack.
Many organizations, including TRU, find the Incidents component of Microsoft 365 Defender valuable, as it provides an all-in-one view of security incidents and plays a pivotal role in threat investigations. Remember, the more Microsoft Security tools you integrate, the higher visibility you can achieve.
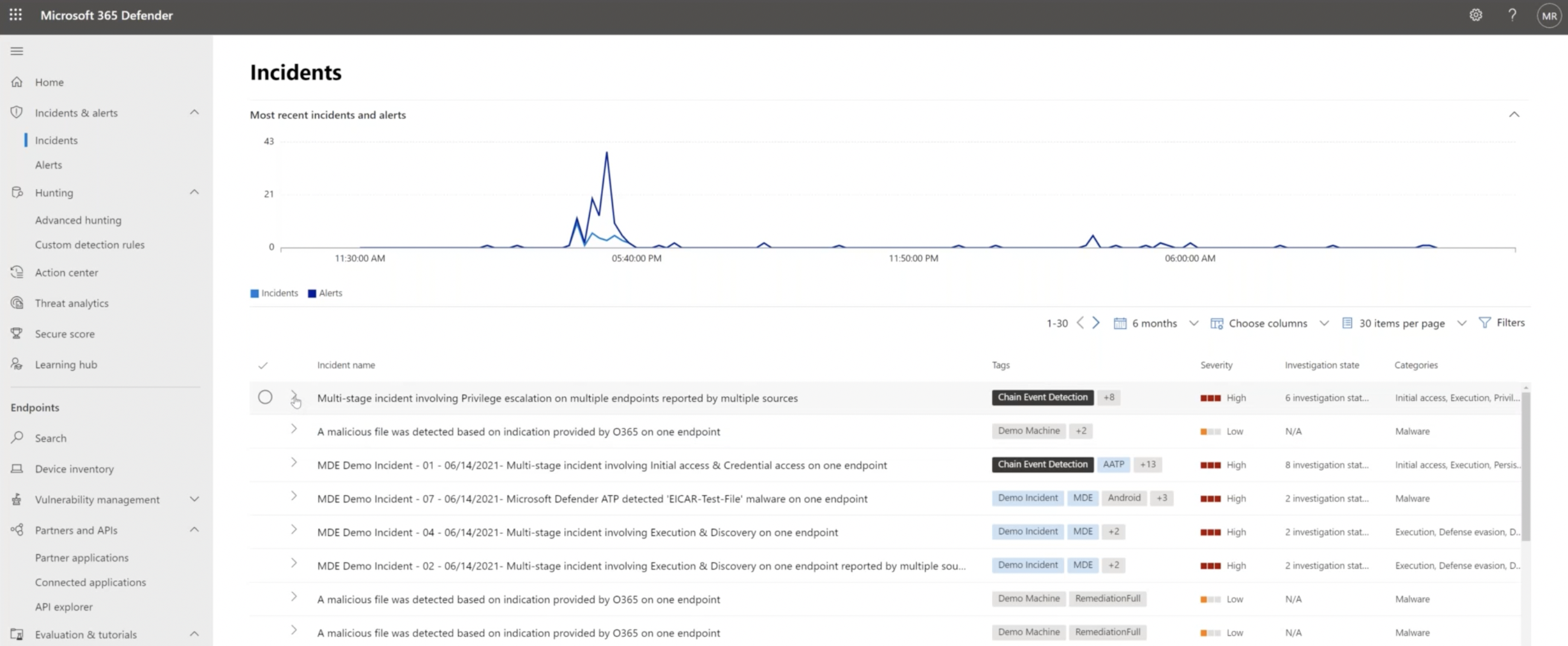
As shown above, the incidents tab of MCAS displays all the assets that would be impacted and the timeline of what happened, and it also provides direction to the source of that alert.
AZURE SENTINEL
If you need an advanced look into security incidents, then you can set up Azure Sentinel. It aggregates the logs from Office 365, 3rd party products like firewalls and runs heuristics based on which alerts are created. The more data and information that are connected to it, the more queries you can run, so it is important to feed data into it.
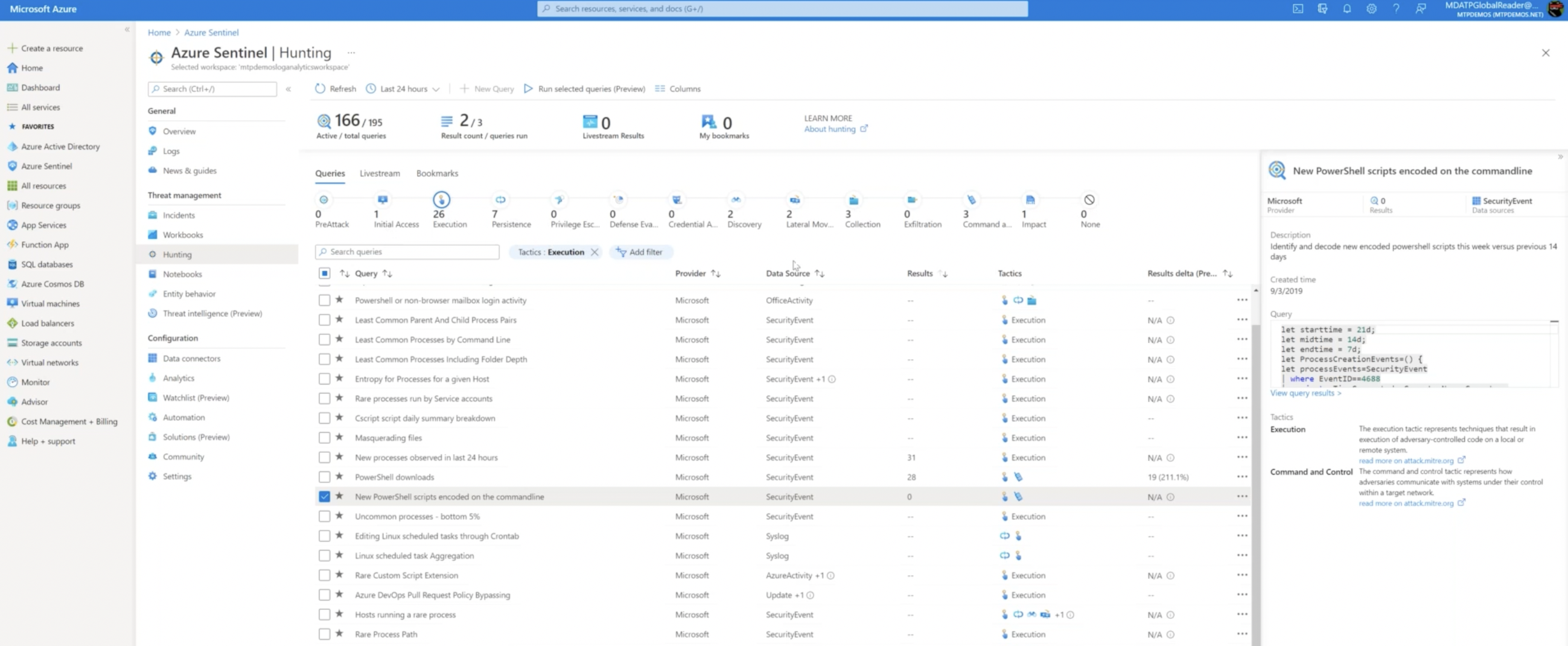
These are some powerful ways to get a good view into each application that makes up your cloud environment and stay update-to-date on security efforts.
Cloud Security Lessons Learned at TRU
From working alongside TRU and helping with the configuration of its cloud security setup, there were some common takeaways that are worth highlighting:
Microsoft Cloud Security technology develops at a fast pace so training can quickly become outdated before it is even applied.
Getting the configuration right makes a huge difference so it’s worth spending time to ensure your cloud security solutions are set up effectively.
Microsoft has a large portfolio of tools that are complex and broad. Having a reliable partner that has done it before can really help to streamline the process.
What is Our Recommended Cloud Security Approach?
If you are looking at a cloud security approach in your environment, then the three basic steps are:
- Check your Security Score – Assess your security maturity and check your Microsoft Secure Score to measure your security posture.
- Take a Risk-Based Approach – Identify the main organizational security risks in your environment.
- Proactive Threat Hunting – Proactively identify potential risks using threat hunting and consider utilizing Azure Sentinel if you aren’t already.
Going forward from here, if you are ready to equip your environment with the appropriate cloud security, you may want to explore Microsoft Security Workshops that are available.
There are additional support resources to help you along your cloud security journey, such as our Security Mentoring Service that is tailored to your unique security requirements. If your organization qualifies for the Microsoft FastTrack Program, then you have another option for an effective approach to adopting Microsoft cloud-based services seamlessly.
Get in touch with our team to get a Microsoft Security assessment today and take a step towards fulfilling your cloud security needs.
Microsoft Cloud Security Frequently Asked Questions:
- Is there a way to view what Microsoft products a given type of Microsoft licence (A1, A3, A5) has access to?
Yes, there is a visual representation of products one has access to depending upon the license. It was created by an ex-Microsoft employee, and it’s called M365 Maps. It is a great site as it tells you what you have access to and also shows you different ways of purchasing and licensing different products. - Does it make sense to block end-user access to OneDrive and SharePoint on un-managed devices?
In the TRU environment they have not implemented Intune or Endpoint manager for their devices, so the devices are not managed according to Microsoft. They are working on that and it will be implemented as people bring their computers back to campus. But there is no plan to prevent access to those resources as they will be moving to Multi-Factor Authentication which will help to secure that access. - Multi-tenant access is becoming more and more the standard. Employees have work access and their kids’ school accounts. Access and distinguish accounts seem to be primitive and still confusing for basic users. Any comments about that?
BCNET is a great resource as they have a community of practice working in this area and it is recommended to look into the community of practices to see how more mature organizations are approaching it. - What’s been your experience with submitting email and URL samples to Microsoft? what happens on the backend after submission?
A lot of it is a blackbox, and you can’t go in and see the submissions that have been put through. But once Microsoft identifies that it is malicious, the next time it comes through it will be detected as malicious. You can also report things that are clean to Microsoft and it eventually learns that this is okay for your environment. The more you report the more accurate the filter will be, so make sure you mark your activities properly. - How do you deal with your staff/faculty having local admin access on their machines? Any solution to control or limit access?
Yes, using Local Administrator Password Solution (LAPS), works great for just-in-time help-desk control and local admin access. You can also implement Jam and use PDQ that is pretty effective in managing applications. - “Zero Trust” gets thrown around quite a bit in Microsoft’s security communications, how does it play a part in the Microsoft security suite?
Zero Trust is really about the ability to look at the context, and ask questions such as:
– Are users using a trusted device?
– Are users in a trusted location?
– What are users trying to do?
Zero Trust must be a consideration between your current architecture and the plans for your future architecture and there are a lot of security components in the Microsoft 365 Security suite that align with that. The key components of Zero Trust architecture include Azure AD, Conditional Access, Microsoft Cloud App Security, Privileged Identity Management, and more. - What’s your recommended approach for training a Security Team on the MS Security Portal?
Within the Microsoft Security console, there is a learning hub that includes documents and resources to provide information to help train your security team. Since the expanse of resources is so extensive, some level of investigation may be required to narrow down on specific topics, but it is a good up-to-date resource for training materials. There is also a variety of Microsoft security, compliance, and identity workshops available that can help organizations train their teams on specific elements of cloud security. - How do you identify and deal with false-positive alerts?
Initially, you might have to look at all kinds of alerts to understand which may be false, this helps you differentiate between what kind of activity you should be expecting and what is out of the ordinary. Even if you cannot go through all of the alerts, it is important to get insights on a sizeable subset that represents the alerts accurately. You can tune policies to make them less sensitive and create exclusions for users that are conducting legitimate and benign activities. - We’re not allowing students to sign into Teams but can’t find a way to prevent it from installing on their personal machines when they install their Office 365. Is there a way to set a security policy that would disable or deny that app from being installed?
There are not many changes to packages that are installed for end users. This is a difficult change to make as a policy may affect both staff and students. Even when it comes to the installer itself, it is complex to control what a user chooses to download on their computer, especially if it is a personal one. But you can change permission inside of Microsoft Admin so that they do not have access to sign into MS Teams. Additionally, you can use Microsoft Intune to uninstall or explicitly remove MS Teams from the bundle.
Author: Dave Steeves

Dave Steeves, CEO, and Founder of Steeves and Associates has been on the cutting edge of technology throughout his career with the past 25 years running his own company as Microsoft 1st Canadian Cloud Partner and one of the first Microsoft Certified Partners. Steeves has always been an early adopter and visionary, helping his clients adopt disruptive emerging technologies managing risk with careful selection of viable use cases to create value. When not tinkering in tech Dave enjoys hockey, skiing, and spending time with his family.

