The New Normal: Securely Accessing Corporate Resources Remotely
At Steeves and Associates, we understand that getting used to this new way of working, with a predominately remote workforce is impacting many businesses across the globe and it prompts questions such as:
- How do you enable a remote workforce?
- How can organizations safeguard identity and information access?
Organizations are challenged by having employees working on a mix of both company and employee-owned devices, accessing services remotely, so how can IT teams protect corporate information, and importantly identify people who hold the keys to corporate assets.
Read on to find out our recommendations on how to achieve this.
Throughout this blog, we are aiming to answer the following questions:
- How can organizations safeguard identity and information access?
- How can you configure multi-factor authentication (MFA) for users?
- What other methods are available to ensure secured authenticated access?
- What’s required for providing secure offsite access to corporate resources?
- What are my options if I don’t have a scalable VPN access solution?
Check out our Remote Working On-Demand Webinar Series here >>
Quick Identity and Access Wins
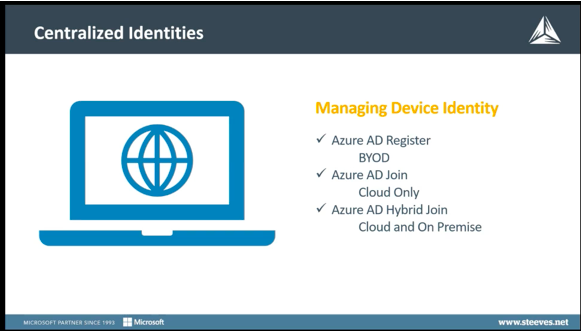
Centralized Identities
You might be wondering what’s the best strategy for connecting computers to your tenant, and the answer is: it depends!
- Azure Active Directory (AD) Register is for Bring Your Own Device (BYOD), aka personal devices, and the user will sign on to the device with their local work account.
- Azure Active Directory (AD) Join, which is cloud-only and allows users to sign into their device with their company email address. This authenticates your Active Directory and even though this is a cloud-only option, you still have on-premises servers and the identity gets integrated with your resources through the synchronization of Azure AD Connect.
- Azure Active Directory (AD) Hybrid Join, is connected to AD and the cloud, it can be managed by Configuration Manager or Co-managed with Microsoft Intune.
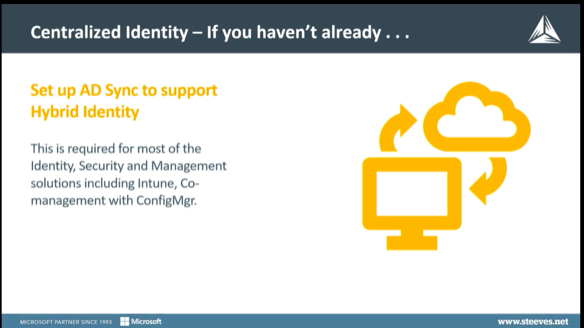
If you haven’t already, you probably need to synchronize your on-premises Active Directory with Azure Active Directory, as you need this to support Hybrid Identity. It’s required for most identity, security, and management solutions including Intune, Co-management, and Configuration Manager. Devices that are hybrid AD joint, are owned by an organization and are signed in with the Azure AD account, belonging to that organization. They exist in the cloud and on-premises.
If you have on-premises servers, you’ll have an Active Directory to manage your user security. You will want to synchronize those user identities to your Office 365 Tenant so that users only have one identity to remember. Also, administrators only have to deal with one synchronized identity.
Microsoft has developed a very nice program to do this and it’s called Azure AD Connect. It has a wizard-driven install and when you install it, you will need to make some choices for synchronizing your directory. The default and recommended way to use this is a ‘password hash synchronization’ which supports single sign-on.
Note that there are other methods to synchronize, such as pass-through synchronization but if you need to get your tenant synced, then the default method is typically the way to go.
Watch Our On-Demand Webinar:
‘Securely Accessing Corporate Resources Remotely’
Watch the webinar now to learn insights from our senior identity and access consultants on the optimal approach to securing access to your corporate resources.
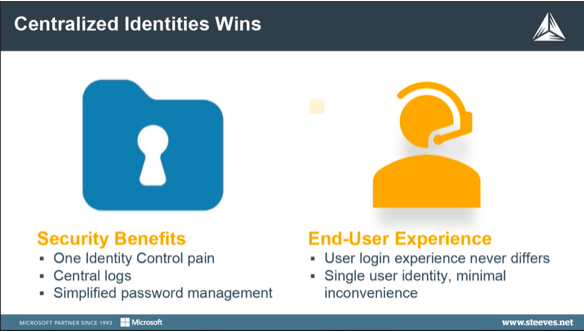
If you haven’t already implemented Centralized Identity in your Azure AD, installing Azure AD Connect and running your organization immediately has the opportunity to realize some significant security benefits.
- Authentication is no longer dependent on the availability of your on-premises domain controller.
- Users can be authenticated from any internet-connected device.
- From a user perspective, the centralized identity is nearly invisible, and makes their lives easier.
Super Easy Win #1: Single Sign-On
It’s worth setting up single sign-on with your software-as-a-service apps, users really love this! The same username and password are used to authenticate a myriad of resources such as:
- Service now
- Box
- DocuSign
- Salesforce
Users will be able to access applications from the Office 365 portal or through the Azure AD ‘my apps’ access panel. Administrators can centralize user account management and automatically add or remove user access to applications based on group membership. There may be a few issues to work through like not all browsers behaving the same, but in general, this is a big win.
Super Easy Win #2: Self-Service Password Reset
Not only will it free up your administrator time, but users will be able to reset their passwords without waiting for IT. Consider doing this at the same time as you implement Multi-factor Authentication (MFA). Now, this is an Azure AD Premium service, but the cost benefits are easy to justify.
- It will free up your helpdesk time
- There are nice tutorials online
- It’s easy to do a staged rollout
Quickfire Benefits of Centralised Identities
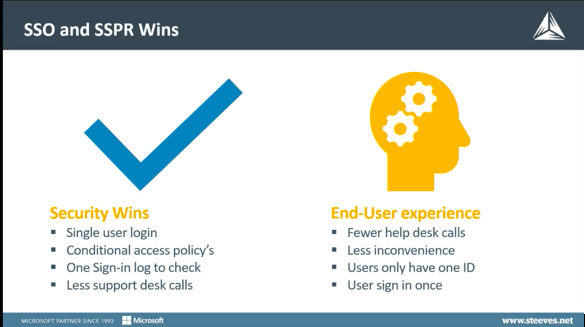
For administrators:
- You have one identity to manage
- You can apply Conditional Access policies
- There’s one sign-in log to check
- There are fewer support calls
For users:
- It’s a more convenient
- There’s only one ID to remember
- Users sign in once
Learn More About Enabling Your Remote Workforce Securely with our on-demand webinar: ‘Securely Accessing Corporate Resources Remotely’
WATCH NOW >>
Conditional Access
The modern security perimeter now extends beyond your organization’s network to include user and device identity. You can utilize these identity signals as part of their access control decisions. Conditional Access is the tool used by Azure Active Directory to bring these identity signals together to make decisions and enforce organizational policies. Conditional Access is at the heart of the new identity-driven control plane. Conditional Access policies, at their simplest, are ‘if/then’ statements; if a user wants access to a resource they must complete an action.
There are a couple of ways to implement Conditional Access, one is called Security Defaults, and the other is through building your own Conditional Access policies.
What are Security Defaults?
These days, every Office 365 plan comes with the option to enable Security Defaults. This is a great win for smaller organizations as it’s easy to set up. Basically, you just need to turn on one switch. Once this has been switched on, it will set up recommended preconfigured settings.
So, when you switch on Security Defaults this is what will happen:
- It will require all IT admins to use MFA (Multi-factor Authentication)
- It will require all users to register for MFA
- Users will be challenged for MFA whenever necessary
- It will disable legacy authentication, which you can’t do with MFA
When you enable secure defaults, all users must now register for multi-factor authentication. So it’s important to do a bit of planning and communicating. The cool thing is the process of signing in after enabling Security Defaults will actually walk the users through registering for multi-factor authentication using the Microsoft authenticator app.
Users will have 14 days to complete the process, so they will have plenty of time. The 14-day countdown is tied to each user, not when you enable secure defaults. The 14-day countdown begins the first time a user signs on after you enable Security Defaults.
If I Block Legacy Authentication Will It Break My Existing Applications?
Yes, it could break your existing applications because up until Outlook 2013 they didn’t support legacy authentication. You’ve got to make sure you have Outlook 2013 or newer, and it’s the same for iOS, you want that iOS to be version 13 or higher. For Android, and even for iOS, the recommended app for looking at your email is the Outlook Mobile App.
Is There A Way to Test Conditional Access Policies?
As an IT/ security administrator, the last thing you want to do is lock users out, so in the Conditional Access Portal there’s something called the ‘what-if tool’ so you can build your Conditional Access policy and see what happens to a particular user and how it affects their access.
What Should Be Considered When Using Security Defaults?

- The users will only be able to use the authenticator app for MFA
- The authenticator app works Really well and it’s easy to use but some organizations that will be an issue as they need to use other second-factor methods
- If you have requirements for custom Conditional Access policies, you will have to leave secure defaults off and build your own set of Conditional Access policies.
Because Security Defaults will block authentication against the old protocols. You will need to do a little planning again, you wanna make sure your users are using current apps like Outlook from the Office 365 subscriptions.
In general, Security Defaults are a fantastic quick win for many organizations and, if you have a relatively new tenant that was created after October 22nd, 2019 your Security Default should already be enabled. If you’re using the baseline security policies then these were replaced by Security Defaults back in February. If the Security Default sounds limiting or you see yourself growing out of them, you need to look at setting up Conditional Access policies.
For insights into the tools and technology that will enable your workforce to work remotely, securely – Watch Our 4-Part Webinar Series >>
Is It Possible To See The Effects Of A Conditional Access Policy By Having Aad Report Back Without Actually Blocking The Access?
In the Conditional Access policies, there are three options. You can turn it into a ‘report-only’ mode, where it doesn’t block the user it just reports into the science console or you can put it ‘on’ or ‘off’.
Multi-factor Authentication
It’s without a doubt, worth implementing MFA for all users, as it really does an incredible job at securing identities.
According to Dark Reading, “Access credentials in the form of email address and passwords are the two most compromised data types. 44% for email addresses and 40% for passwords.”
With the above stats, you can see why just turning on MFA results in a huge quick win for your organization’s security!
Conditional Access Policies:
When users start complaining about MFA or the thought of implementing MFA, we must reiterate that this is an industry norm now and that it’s the recommended best practice. Using the authenticator app is quite easy, but it’s important to let users know that once they’re setup with MFA, we can turn off the policy that requires them to change their password every few months, which is such a huge win.
MFA Benefits for End-users:
- Reduces the risk of being hacked
- Reduces the number of logins required
- Removes the requirement of changing their password every 120 days.
MFA Benefits for IT Administrators:
- Reduces the risk of being hacked
- Secures access to resources
- Reduces the risk of an attack on admin accounts

Multi-factor Authentication Prerequisites Before Implementation:
- If you’re a cloud-only environment, there are no prerequisites – you’re ready to roll.
- If you have a Hybrid Identity Scenario, you must have Azure AD Connect.
- If you have on-premises legacy applications published for cloud access, you’re going to have to install the Azure AD application proxy.
- If you’re using Azure MFA with RADIUS Authentication, you need the network policy server and you have to make sure your users are using a current version of Outlook.
- Greater than Outlook 2013 and on the Apple devices, iOS has to be iOS 12 or later, as the legacy authentication protocols aren’t supported by those older applications.
Multi-factor Authentication Quick Wins:
After you turn on MFA for all users, you will have reduced the chance of their identities being compromised.
Check out our webinar ‘Securely Accessing Corporate Resources Remotely’ to discover even more ways your organization can access corporate resources remotely and securely. Including, Privileged Identity Management Documentation, Identity Secure Score, and more!
With the FastTrack program, we can help you see your journey through. We work with you to plot a course and typically set up a regular cadence based on your time frame to help guide you and add new features.
There are some funded workshops or assessments, including some new ones for remote working, MS Teams, security and compliance. Please reach out to us if you’d like to discuss it. There’s no obligation, you can work with one or multiple Partners or Microsoft directly across different workloads.
Enabling Secure Access – Resources to Get You Started
Azure Active Directory documentation
Set up Multi-factor authentication
Privileged Identity Management documentation
Author: Keith Braun

Keith Braun is an experienced Microsoft 365 Specialist at Steeves and Associates. He brings over 20 years of professional IT consulting experience to our team, and as a certified Microsoft 365 Security Administrator, he is focused on Microsoft 365 Security Solutions. He has worked with these tools early through the Microsoft 365 Business license which has a number of these security products for organizations of up to 300 users. Braun also holds a number of certifications from Microsoft including MBBS and Technology Specialist – Dynamics.

