How Can Organizations Enable a Remote Workforce Securely?
In response to the remote working situation that many people have found themselves in, we have put together a webinar series to help you leverage resources, most of which you already have access to, in order to support your staff while working remotely, and also to maintain remote work security. Additionally, we recognize the uncertainty of these times with cost-cutting and less funding, organizations need help. We hope to help you with some of the challenges that you may be facing.
Check out our Remote Working On-Demand Webinar Series here >>
Through Microsoft’s FastTrack program Steeves and Associates provides organizations with guidance on how to deploy the main cloud workloads and provide additional advice at no additional cost. These services are provided free of charge to organizations with at least 150 seats. If you are interested in learning more about our Microsoft FastTrack complementary services, please get in touch.
This blog covers the quick wins that your organization can realize by using your existing office licensing and technology.
Maintaining Productivity & Remote Work Security Amid Uncertainty
With most businesses closing their doors and asking their workforce to work from home, the need to effectively work remotely has skyrocketed in the past few weeks. It’s probably one of your company’s number one priorities and this might be especially daunting considering this global health crisis is rapidly evolving and has no end in sight.
Amidst this uncertainty, there are some quick and easy wins that can help your organization to enable remote working success while ensuring that your corporate data is secure. It basically falls on your IT department to be able to adapt to the increase of users working remotely.
Remote Work Security | A Microsoft Webinar by Steeves & Associates Now!
Check out our Microsoft webinar today to learn how you can support a remote team and ensure remote work security with Microsoft Teams, Endpoint Management, Active AD, and more.
The Barriers to Effective & Secure Remote Working
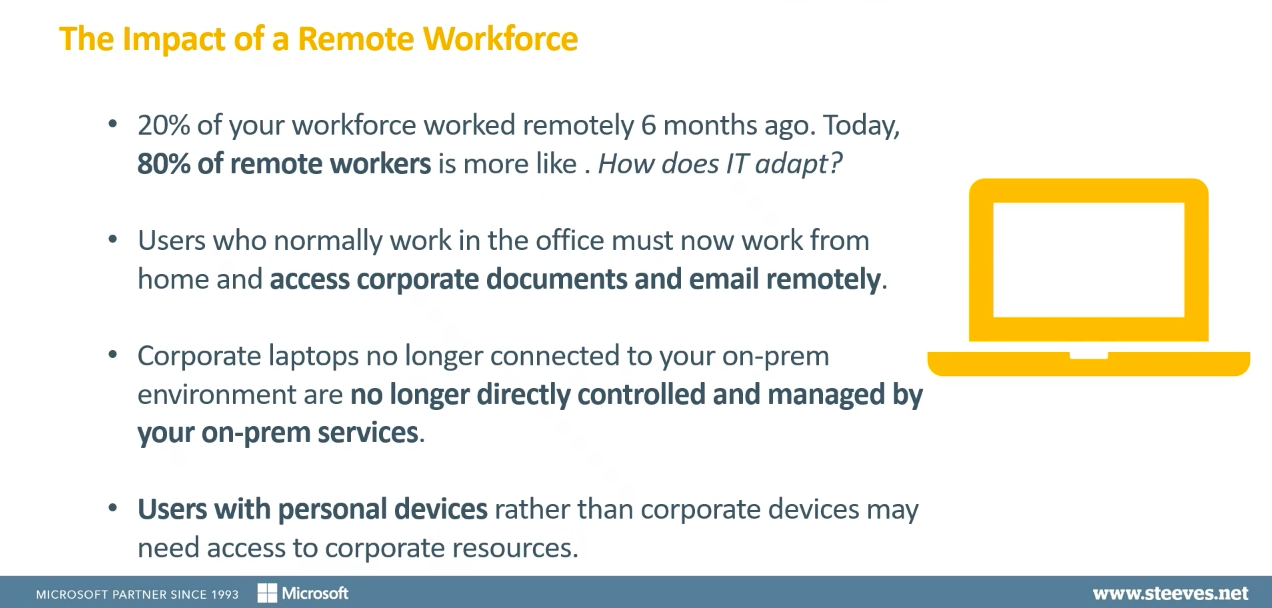
The problem, which you will be aware of, is that people who normally work at the office are now working from home. They still need to be able to access corporate documents and information remotely and securely.
There are other factors such as corporate laptops and devices no longer being connected to your on-premises environment or employees using personal devices, meaning they are no longer being managed directly by your on-premises services in the regular way.
On top of all of this, it’s important that the user experience stays familiar and consistent. We don’t want people to have to learn a whole new way of doing things and, most importantly, any data that’s being accessed needs to be done in a secure manner and from devices that can be trusted.
So, we need to find ways to ensure that a user can access the files and the data they need to allow them to do what they need to do to fulfill their role.
Learn More About Enabling Your Remote Workforce Securely
by Watching Our 4-Part Webinar Series >>
‘The Ask’ From Business
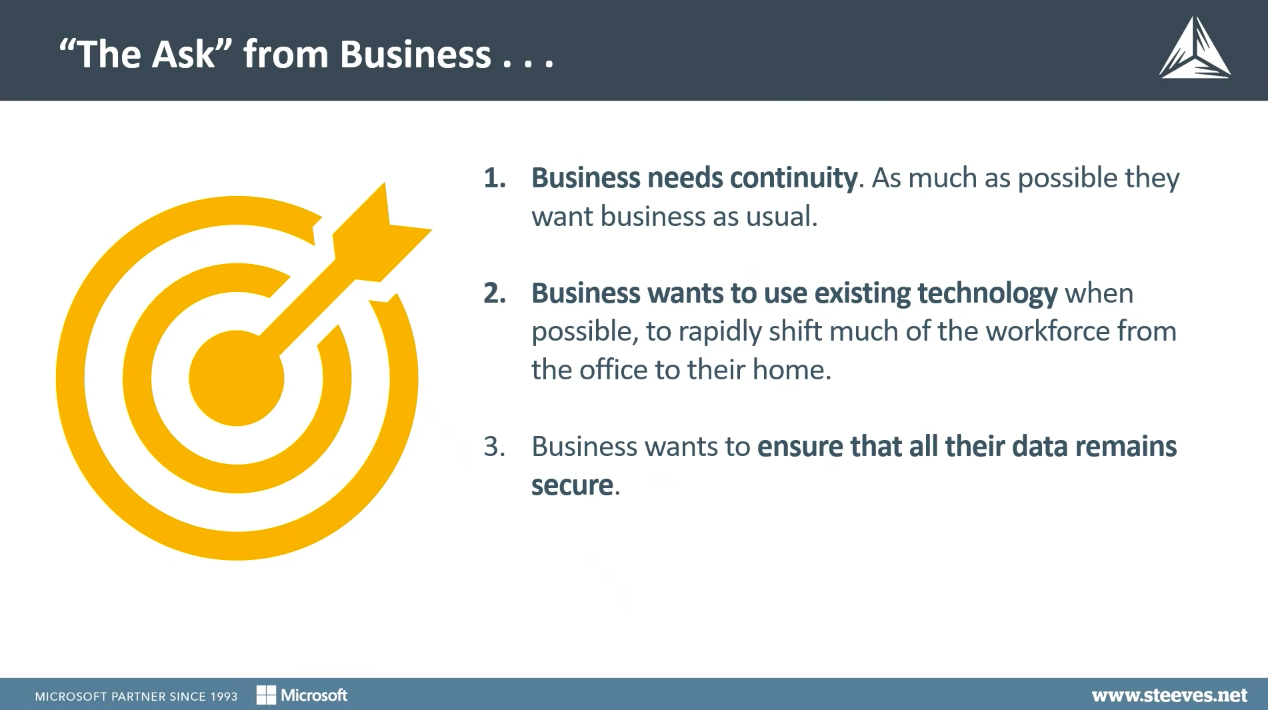
The above image details the three key ‘asks’ that businesses are requiring from their remote workforce:
- Business Continuity
- Use of existing technology
- Remote work security and secure corporate data
We understand that none of this is easy to do; it’s hard to continue ‘business-as-usual’ when you’re also being required to use the existing technology that isn’t set up for a remote workforce.
Finally, businesses want to ensure that any data that is being accessed remotely is going to remain secure.
Challenges for Enabling Secure Remote Working

The challenges that IT needs to be able to respond to fall into three buckets:
1 – Secured access to resources
-
- When users are working from home, they require access to emails, applications, and files, and this needs to be delivered in a way that is familiar, plus with the user’s identity being secured and authenticated.
2 – Communication and collaboration
-
- As it’s no longer possible for staff to swivel on their chair and tap somebody on the shoulder to ask a question, we now have to find ways to ensure that they can communicate and collaborate, so they continue to have meetings and discussions and work collaboratively on documents.
3 – Endpoint security and management
-
- Ultimately, companies need to be certain that all of their corporate data is secured and that the devices and endpoints that have access to this data are also secure, safe, and managed successfully.
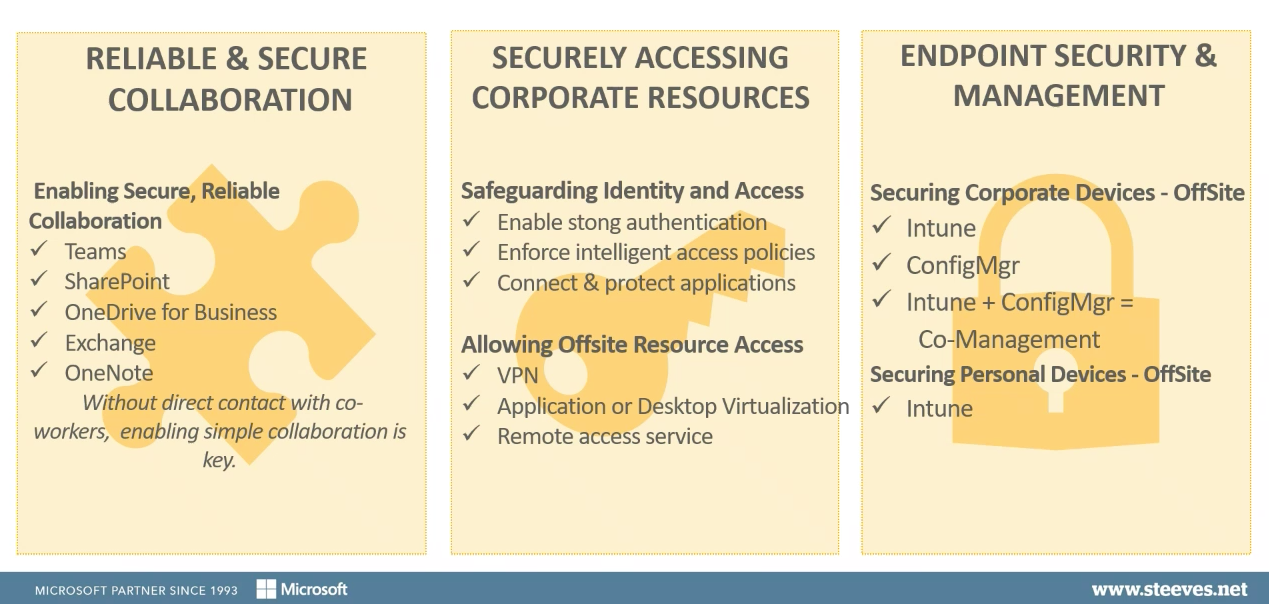
Enable Reliable and Secure Collaboration
Your IT department will hopefully take advantage of as many existing tools as possible. But, one of the assumptions that we have made is that many organizations will have already onboarded some features of Microsoft Azure and Microsoft Office 365.
To facilitate reliable and secure collaboration, we look at solutions such as:
Without direct contact with coworkers, these tools allow users to continue to collaborate and communicate, thus allowing them to continue to work together effectively.
What are the Recommendations for the Initial Set up of Permissioning/Provisioning Levels in Microsoft Teams?
One of the biggest questions that you have to ask yourself and decide upon is whether you are
going to let all of your users create Teams on an ad hoc basis as they need or if you are going to try to control that creation from within the IT group?
If you’re going to try to control Team creation, it’s fairly straightforward to do and it’s just a matter of making a couple of changes in the Azure Active Directory. You’re then able to define a specific ‘user group’ who are the only ones that can actually create a new Microsoft Team. However, that doesn’t stop you from assigning a ‘regular user’ as the owner of that Team. They can do everything that they need to beyond that point and it gives you a good opportunity to ensure MS Teams are created in a controllable fashion.
Is There a Central Permissioning/Security for all of Office 365, Including MS Teams?
There’s not really a single ‘central point’ for this, and part of that is because MS Teams is an all-encompassing kind of application. Within the Teams ‘Administration’ panel you can set some things like:
- How you want to treat guest access
- Whether users can have external meetings
- Whether users can federate with other organizations
- Whether users can federate with Skype users
Some of the other pieces you have to do are within Azure AD portal in your general policies, for example:
- How you configure guest access to your tenant
- Whether you’re setting up any specific B2B scenarios
You really also need to look at this from a SharePoint / OneDrive ‘sharing permissions’ point of view, as these SharePoint policies more or less override any kind of OneDrive or MS Teams sharing.
- Are you going to allow guest access by default?
- Are you going to allow anonymous access by default?
- How do you want to set those kinds of things up?
What are the Best Practices for Allowing Guest Access to MS Teams?
Best practice isn’t really ‘do I allow users access or not’. It’s more about understanding what’s available to you and making sure that it fits your requirements. For example, by granting access to a Teams meeting, are your permissions set up in such a way that you’re granting access to your SharePoint data? If so, you then need to know what you can do to implement restrictions around that.
Deliver Secure Remote Working Access to Corporate Resources
Secure access to corporate resources includes:
- Safeguarding identity with strong authentication
- Enforcing access policies for conditional access
You probably already have a VPN solution to allow your users to access your company’s on-premises resources. If not, you need to consider what options are available that can be set up in a short timeframe. We would recommend looking into an application or desktop virtualization. These are easily available services within Microsoft Azure and other remote access services.
Will Multi-factor Authentications (MFA) Break Outlook for Users?
When you implement MFA, it’s good to have a good communication strategy, basically to tell users how to register for MFA and educate them on the process. In general, if Outlook is newer than 2013 and you have enabled modern authentication in your office tenant – then the process is pretty straightforward.
Will MFA lockout users?
Essentially, it comes down to proper communication with your user group. It’s important to point out that they have access to web apps such as:
- Outlook
- OneDrive
- SharePoint
It may be worth creating a cheat sheet to prompt them on how they can use these tools to have meetings, calls, and share documents etc. Also, it may be useful to detail what some of the steps may be that they can take to troubleshoot and to continue being productive while working from home.
Does MFA work on Android or iPhone?
For both Android and iPhone there’s an authenticator app you can download from the App Store and once you install this, you can register in the MFA registration process. That then creates the second-factor authentication. Microsoft recommends you use the Outlook mobile App for accessing Outlook.
The Importance of Endpoint Security and Management
With a fully remote workforce, it’s as important as ever, if not more important to make sure that corporate devices continue to be secured and managed. You will need to:
- Continue to patch systems
- Ensure patch level remains consistent
- Use an anti-malware product
If you’re currently using Configuration Manager, then you need to look at ways to allow Configuration Manager to continue to manage devices. If you’re using Intune, that’s already going to be taken care of. Plus, there is also Co-Management, so multiple different ways of securing personal devices.
How Does Cloud Management Gateway (CMG) Effect Clients Connected via VPN?
If your clients are already connected by a persistent VPN, then generally those devices are going to be treated as if they are ‘intranet’ devices. So, because the device is our ‘intranet device’, they’re going to be coming back to your on-premises infrastructure in order to access your:
- Management point
- Distribution points
- Software update point
If you’d prefer internet-facing clients to come through your cloud services, then you need to configure your Cloud Management Gateway with a ‘boundary group’ to associate them with. The last couple of bills in System Center Configuration Manager have actually supported that, and once you’ve done that action it’s going to force your clients to use a cloud distribution point that you can configure. This will use both the management point and the software update point that is used by the Cloud Management Gateway. Basically, it depends on how you wish to “shake the traffic” that is connected to your network. If you have a VPN solution, Cloud Management Gateway may not be a requirement.
What is the difference between Co-Management and Cloud Management Gateway? And, do you need both?
Co-Management really just tells a client where to get its instructions from. It doesn’t provide a way for the client to come into your network to get instructions if it’s away from the office (which is the case with most remote workers).
A Cloud Management Gateway, on the other hand, extends the capability of Co-Management by
allowing the Configuration Manager clients, that are on the internet, to connect to a proxy server. This is configured in your Azure tenant. When we set up Cloud Management Gateway, that gateway proxy is created. It’s a service created in Azure and all of the Configuration Manager clients on your infrastructure are reconfigured. This means if they are away from the office, they now know to go to this proxy server and come back through there to your Configuration Manager infrastructure.
So, what Cloud Management Gateway allows you to do, is to truly manage those devices when they are off-premises. Again, it may not be necessary if you have a VPN but certainly if you don’t, this is a quick easy win to get those devices back into a managed state again.
Is There a Way to Not Require MFA for All Users or Locations?
Yes, it’s a custom conditional access policy that you would set, and yes, you can configure that.
For insights into the tools and technology that will enable your workforce to work remotely, securely – Watch Our 4-Part Webinar Series >>
Active Directory Group Policy
Your existing group policies are one of the items that you may want to consider, the longer this pandemic continues. Typically, these won’t be applicable to certain devices, unless you’ve got an ‘always on’ VPN solution that supports it.
Implementing a group policy on new devices and making changes to your policy, can become challenging but many of these policies can be moved into Microsoft Intune, in order to manage the devices when they’re connected to the internet.
Many organizations are already looking at moving their group policy objects into a
cloud solution. This is so that your machines don’t have to be on-premises or be connected to your corporate network. This is a relatively quick win that you could begin to implement.
Windows Virtual Desktop
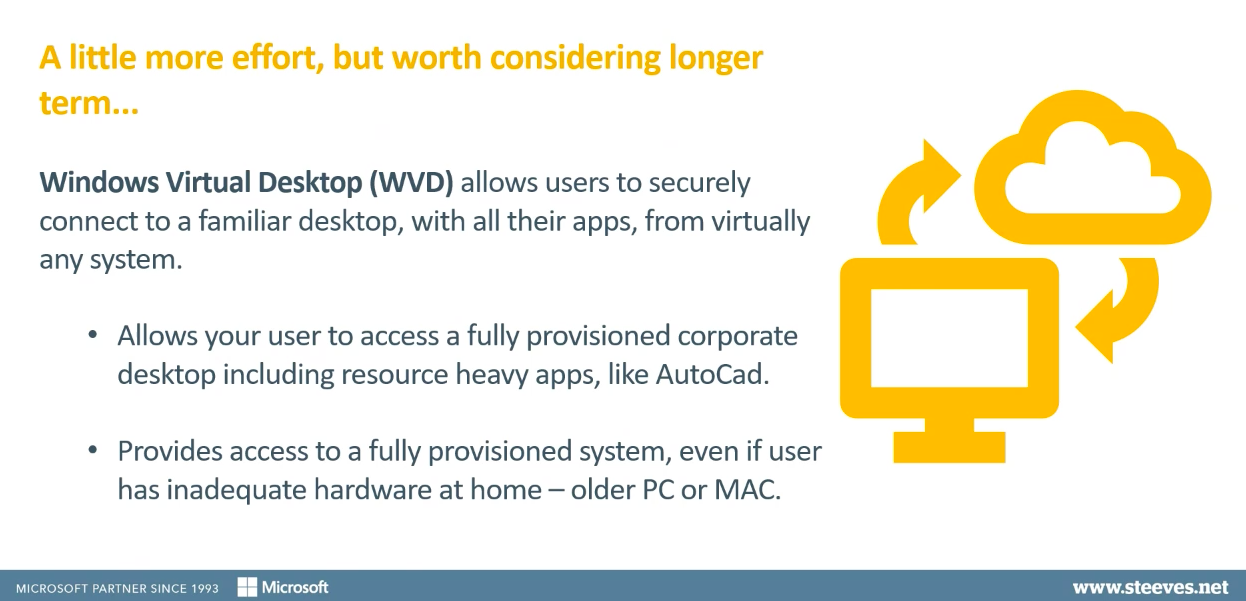
Windows Virtual Desktop requires a little bit more effort but for the longer term, it’s worth considering. This feature is being added to Microsoft Azure and it allows users to connect securely to a really familiar desktop, with all of the apps that they usually work with. Essentially, Windows Virtual Desktop is configured so users can connect virtually from any computer.
It’s a great option if your employees need to use really resource-heavy applications that would be challenging to deploy and manage through Microsoft Intune or over the cloud.
This means that users don’t have to be using a corporate device at all. They’re connecting securely to a virtual desktop that is fully configured and secure. This isn’t going to be an overnight win, but it is worth considering if the current health crisis and remote working continues for quite some time.
To learn about more business continuity options that could work well for your organization, check out our on-demand webinar ‘Enabling Enabling Your Remote Workforce Securely’.
Can Azure AD help Users to Keep Track of Multiple Passwords?
Administrators can set up a ‘single sign-on’ with Azure AD within your cloud services. Then, users would only have to remember one ID if you set it up so that it authenticates access with Azure AD identity.
One of the things that Microsoft recommends is to ‘turn off’ having to change passwords all the time. To do this, you go to ‘Multi-factor Authentication Setup’ and click turn off the ‘require the user to change your password all the time’ feature. It’s as simple as that!
Can Windows Autopilot Fully Replace an Organization’s Current Desktop Imaging Process?
The answer to this question is very dependent on the individual company, but yes, it is possible. With a lot of the enhancements that Microsoft is making to Intune and Autopilot, it’s actually becoming possible to leave the task sequence behind, in favor of Autopilot, and allow Intune to deliver the computer configurations that your company requires. It might not be possible for all the scenarios a standard PC uses for administrative tasks, but it can deliver many, if not all of the customizations that you require.
There are a couple of key points to bear in mind with Windows Autopilot, and the first is that in order to use autopilot, the device ID needs to be registered in Azure AD. That means either the vendor or you will put that ID into your Azure tenant.
Contact Steeves and Associates to find out more about Windows Autopilot and whether removing your desktop imaging process is an option for you.

Ultimately, ask yourself – with the tools that I already have, with the assets that I already own and the licensing I am subscribed to, am I taking advantage of all of the remote workspace assets that I own? And, are there any quick wins that I could take advantage of today to improve my company’s remote access experience?
You may be eligible for a funded Microsoft FastTrack Secure Remote Working Workshop with Steeves and Associates. Inquire with us today to request yours at + 1 888 952 8800 or email info@steeves.net.
Helpful Resources to Get you Started:
- Microsoft FastTrack
- Best Practices for Getting the Most Out of Teams
- Why Start your MS Teams Journey with a FastTrack Assessment?
- Tips for Effective Remote Working
- Endpoint Management: ConfigMgr & Intune Licenses Combined
- Endpoint Management: ConfigMgr, Intune or Both?
- Work remotely, stay secure – guidance for CISOs
Steeves and Associates
![]() Steeves and Associates are the first Microsoft Cloud Partner in Canada and the premier Partner of choice for medium-to-large size organizations. As the Hybrid Data Center, Cloud Productivity and Identity Specialists we are a leader, early adopter and implementer of Microsoft technologies with a reputation for innovation, quality, and in-depth expertise.
Steeves and Associates are the first Microsoft Cloud Partner in Canada and the premier Partner of choice for medium-to-large size organizations. As the Hybrid Data Center, Cloud Productivity and Identity Specialists we are a leader, early adopter and implementer of Microsoft technologies with a reputation for innovation, quality, and in-depth expertise.
Known as the “Trusted Go-to-Partner” by both clients and vendors, Steeves and Associates deliver a senior team of enterprise consultants who average 25 years of experience integrating, implementing and migrating Microsoft solutions into a myriad of complex enterprise environments. Considered to be amongst the best in the industry, you are in working with the right resources to get your questions answered when you need it most with Steeves and Associates.
Considered to be among the best in the industry, Steeves and Associates deliver senior Microsoft technologists with experience integrating, implementing and migrating Microsoft solutions into a myriad of complex enterprise environments.

